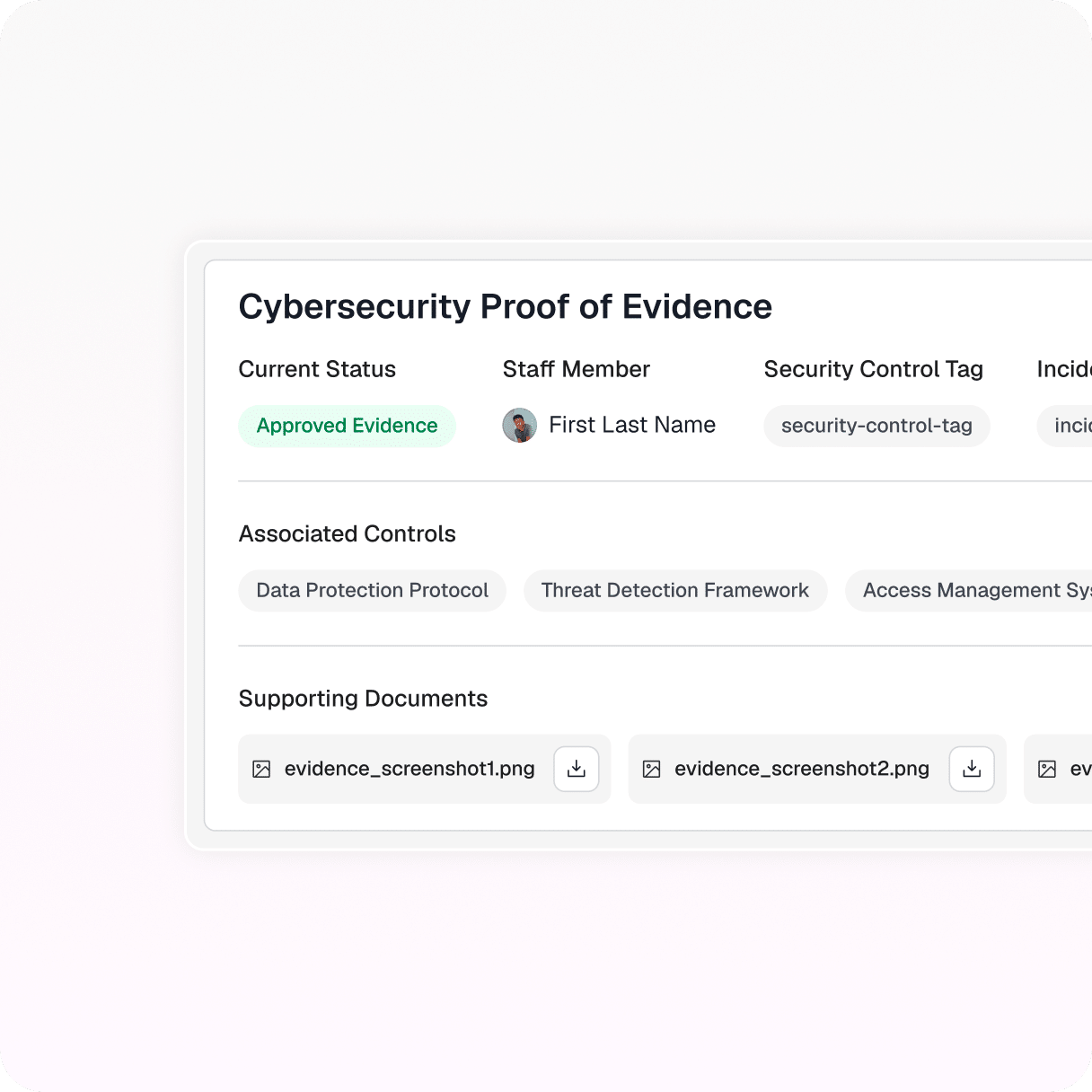
Copla automatically records and stores system activity, uploads, edits, approvals, task completions, and evidence interaction in a tamper-proof audit trail for complete transparency and accountability.
Top-rated on G2 — thanks to our customers.







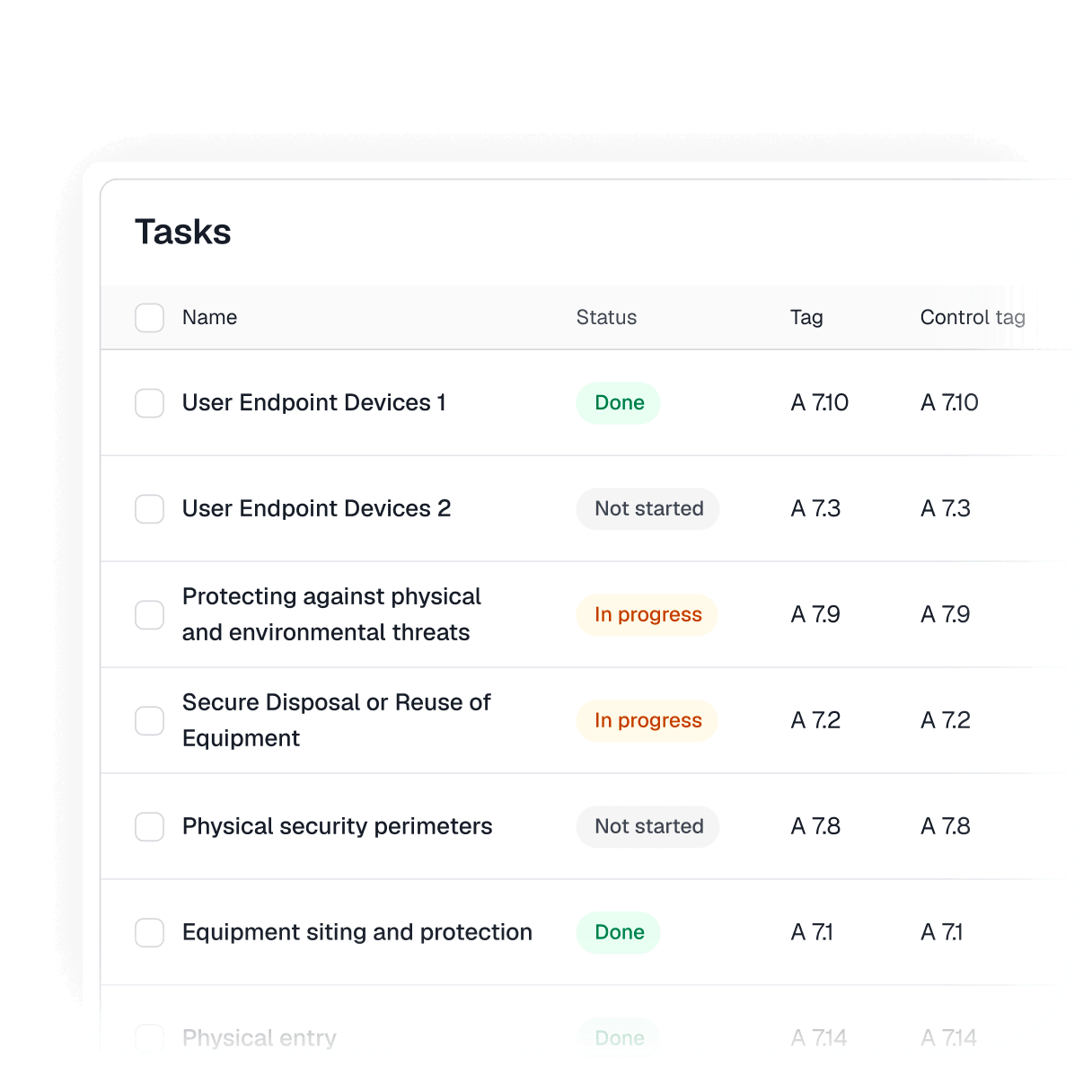
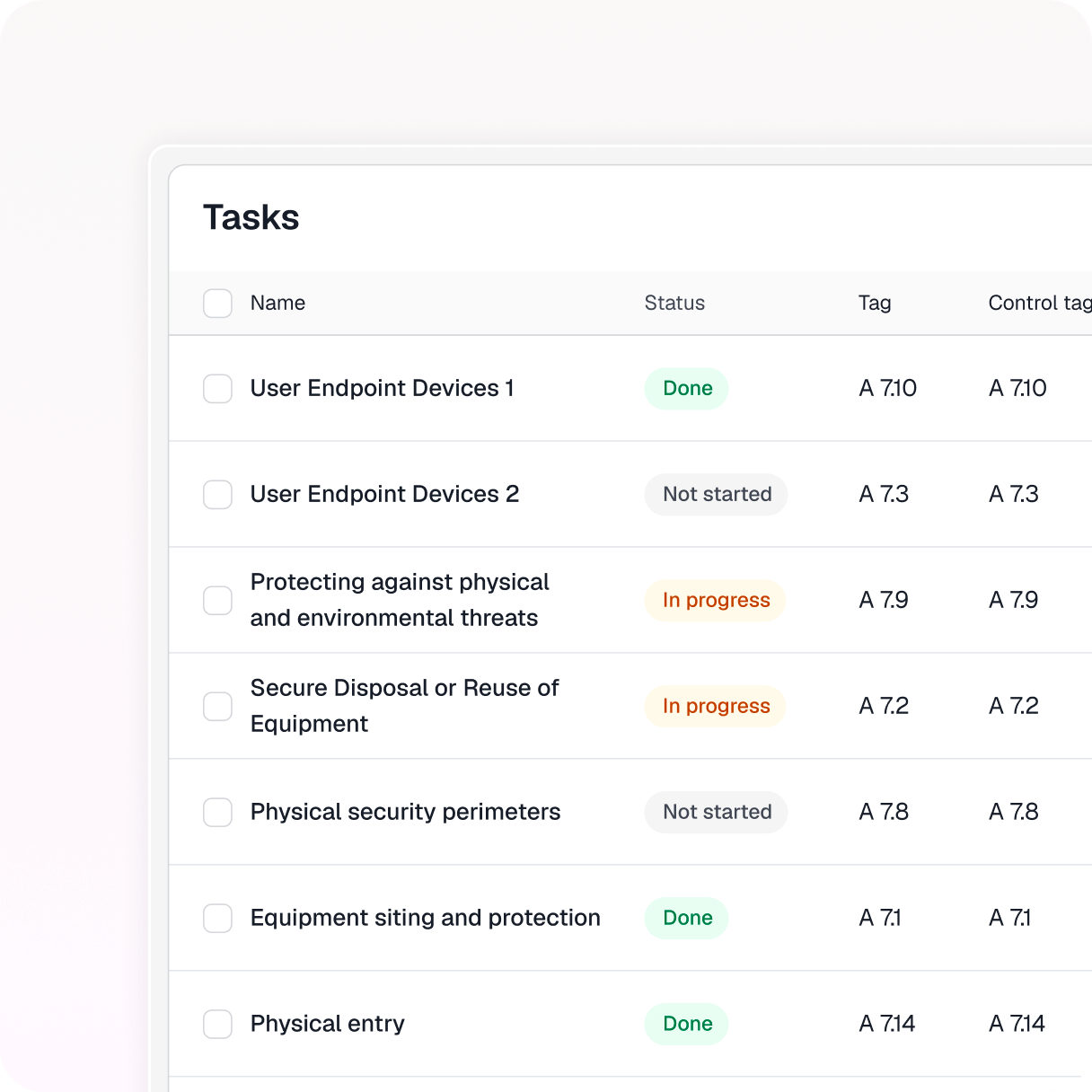
Automated activity logging captures who did what, when, and why for full accountability.
Answer compliance questions in minutes with complete traceability.
Stay continuously prepared through automated documentation and reviews—without extra headcount.
Prove compliance with confidence
Tamper-proof audit trail for all compliance operations
Low-effort oversight
Structured context for each event
Control- and framework-linked events
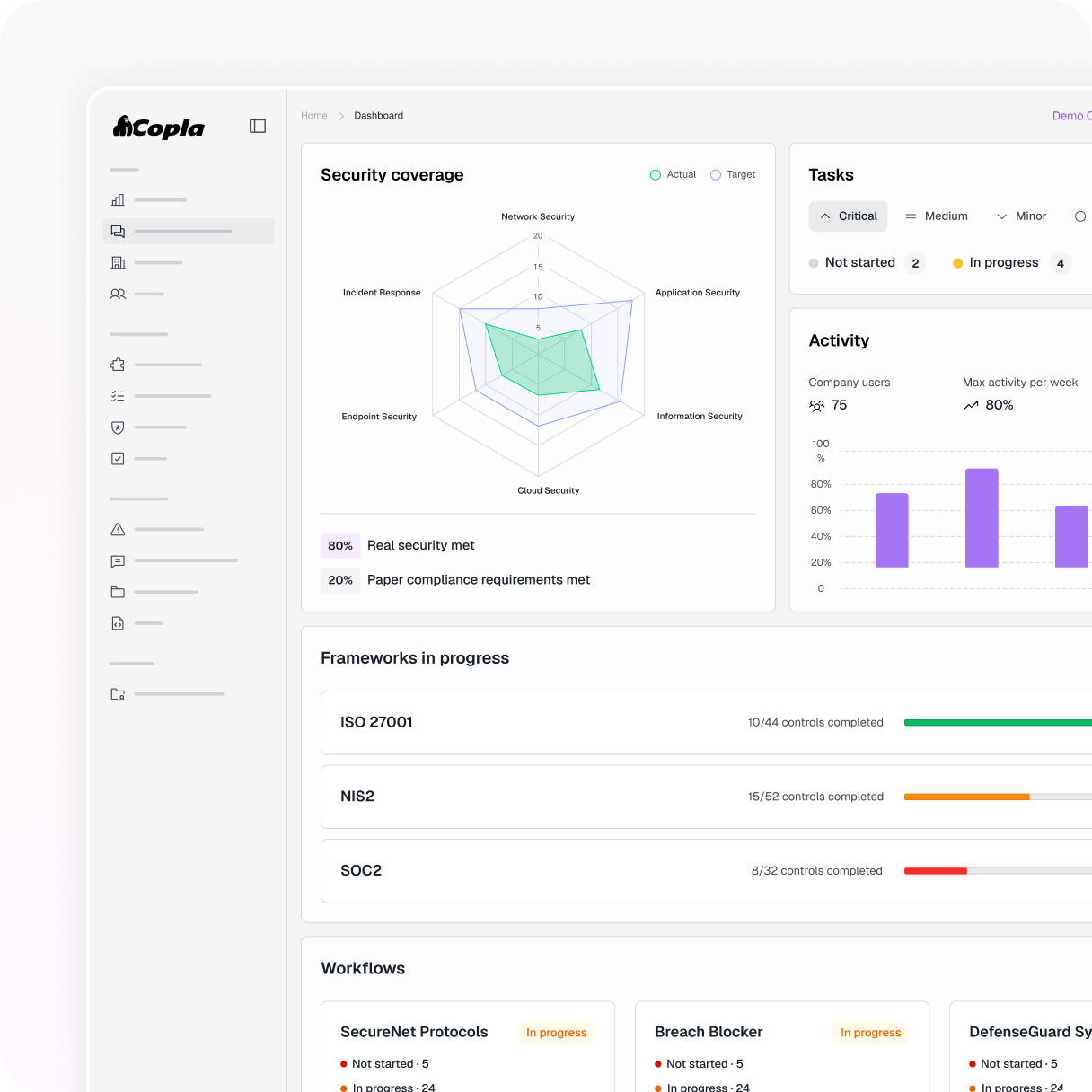
Done-for-you operating model (80%)
Prove compliance with confidence
Tamper-proof audit trail for all compliance operations

Low-effort oversight

Structured context for each event

Control- and framework-linked events

Done-for-you operating model (80%)

— FMpay
— Swotzy
— Axiology

Expertise and delivery



It’s a control-aware and purpose-built platform for compliance: predefined prompts aligned to frameworks, in-line evidence capture, and automatic mapping to tasks and controls.
A structured, question-answer flow that prompts users with predefined questions and instructions, collects evidence, and updates status.
Two-way conversational guidance powered by our GPT-based engine for richer follow-ups and clarifications — timing depends on prioritization.
Yes — artifacts are stored with timestamps, owners, and control mapping, forming defensible audit trails.