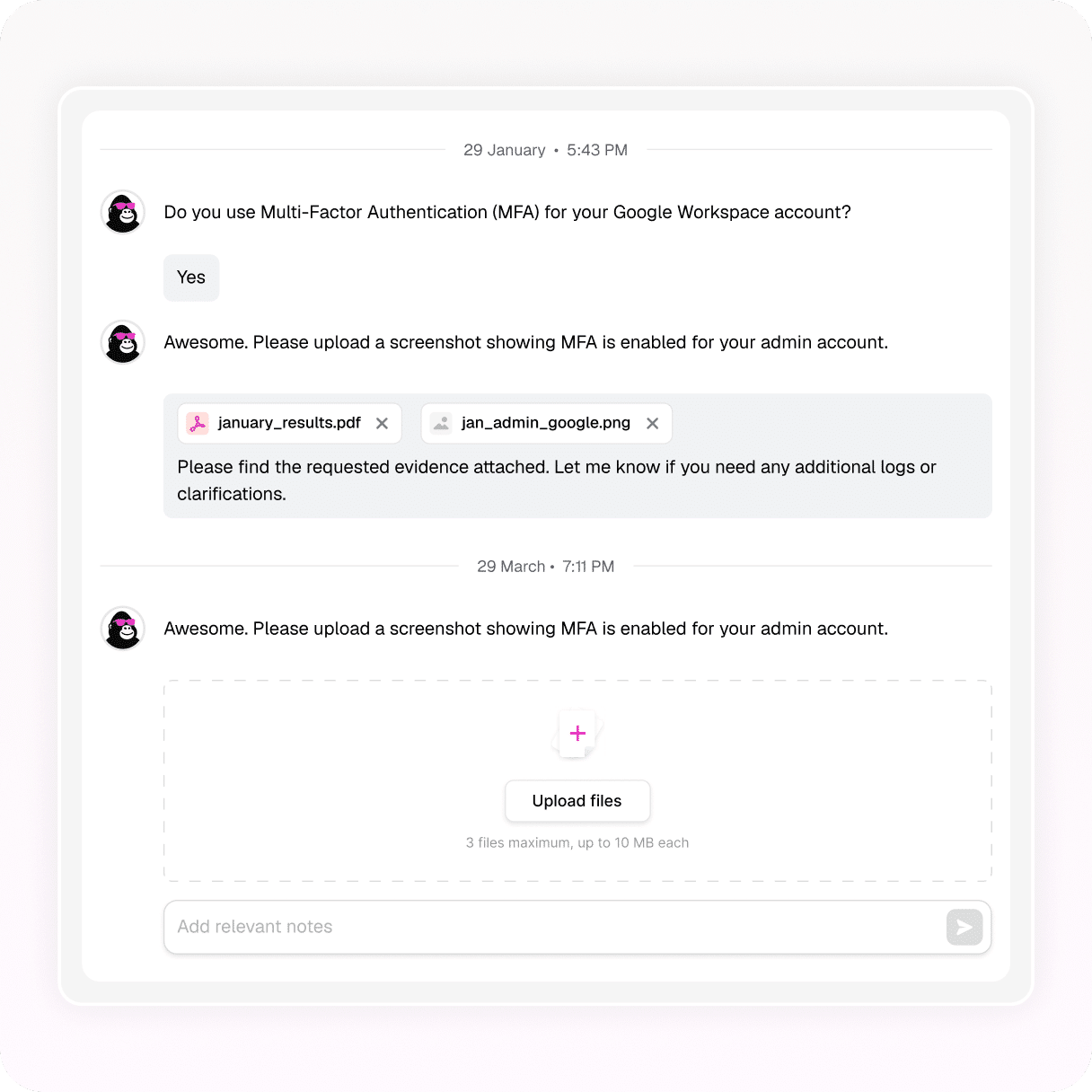
Fully managed scans that uncover misconfigurations and known vulnerabilities across your cloud — and deliver audit-mapped outputs aligned with ISO 27001, DORA, NIS2, and SOC 2.
Top-rated on G2 — thanks to our customers.







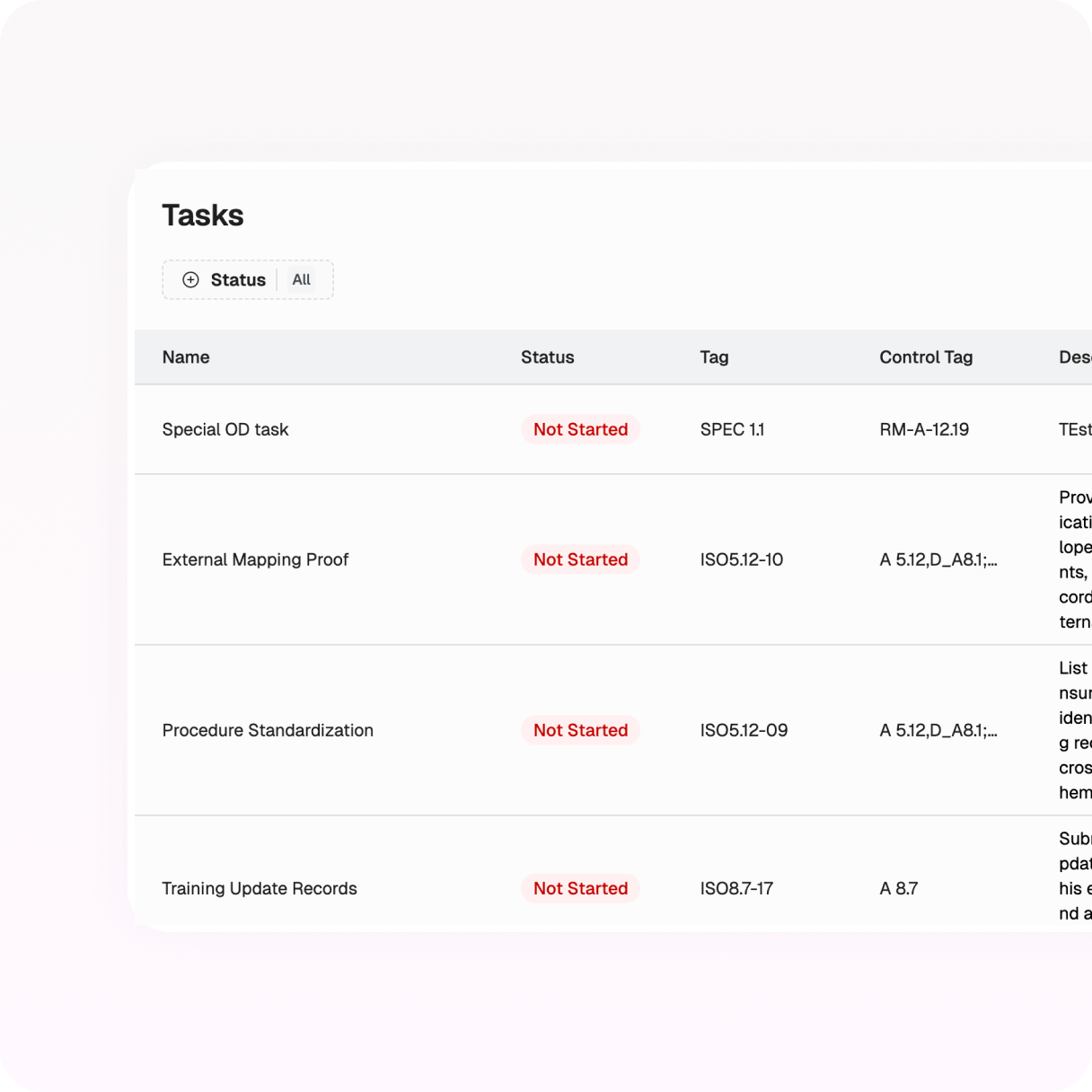
Complete coverage from scoping to result delivery using industry-standard tools.
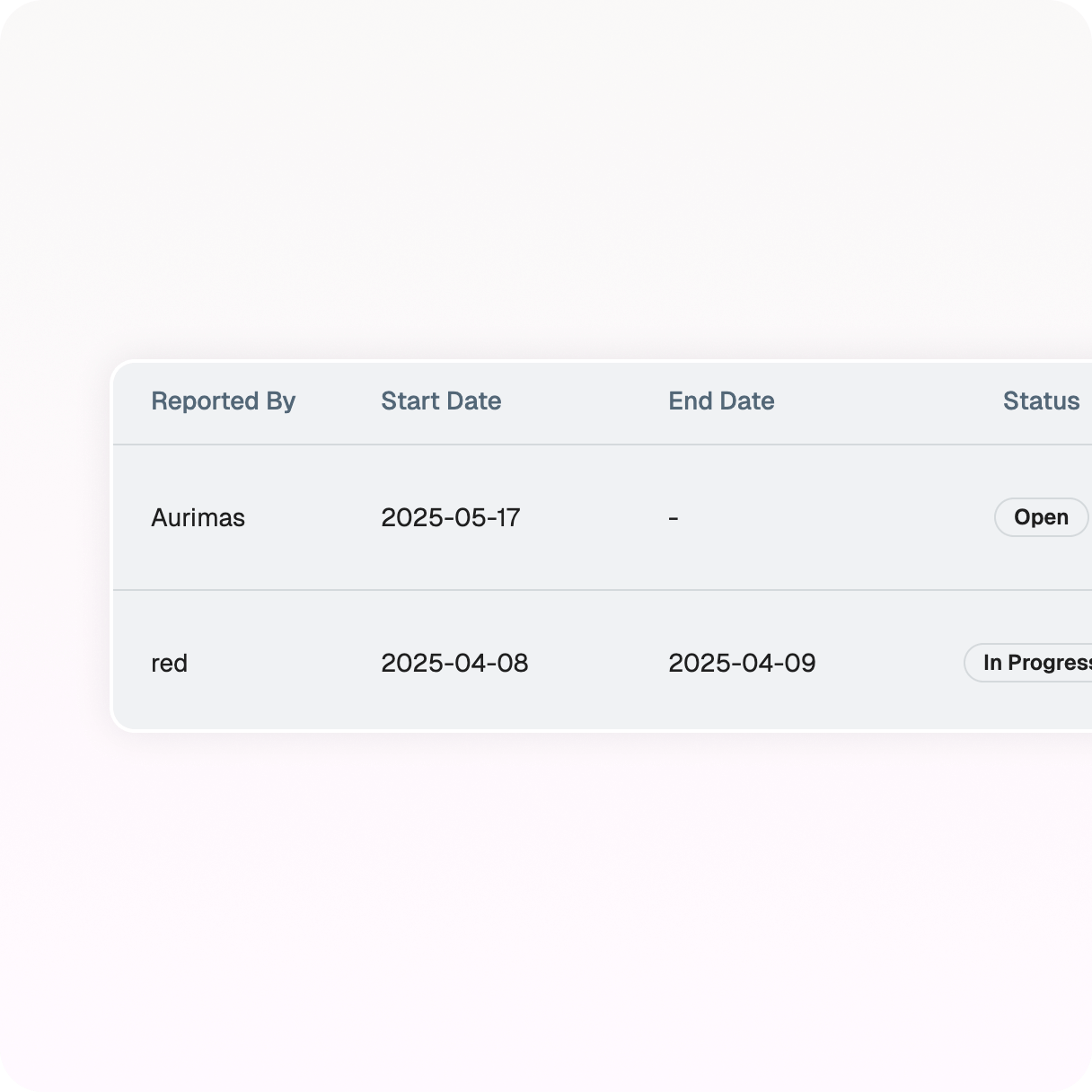
Clear insights with a timestamped audit trail.
One-time or quarterly scans to suit your needs.
Reports as raw outputs or control-mapped for ISO, DORA, NIS2, and SOC 2.
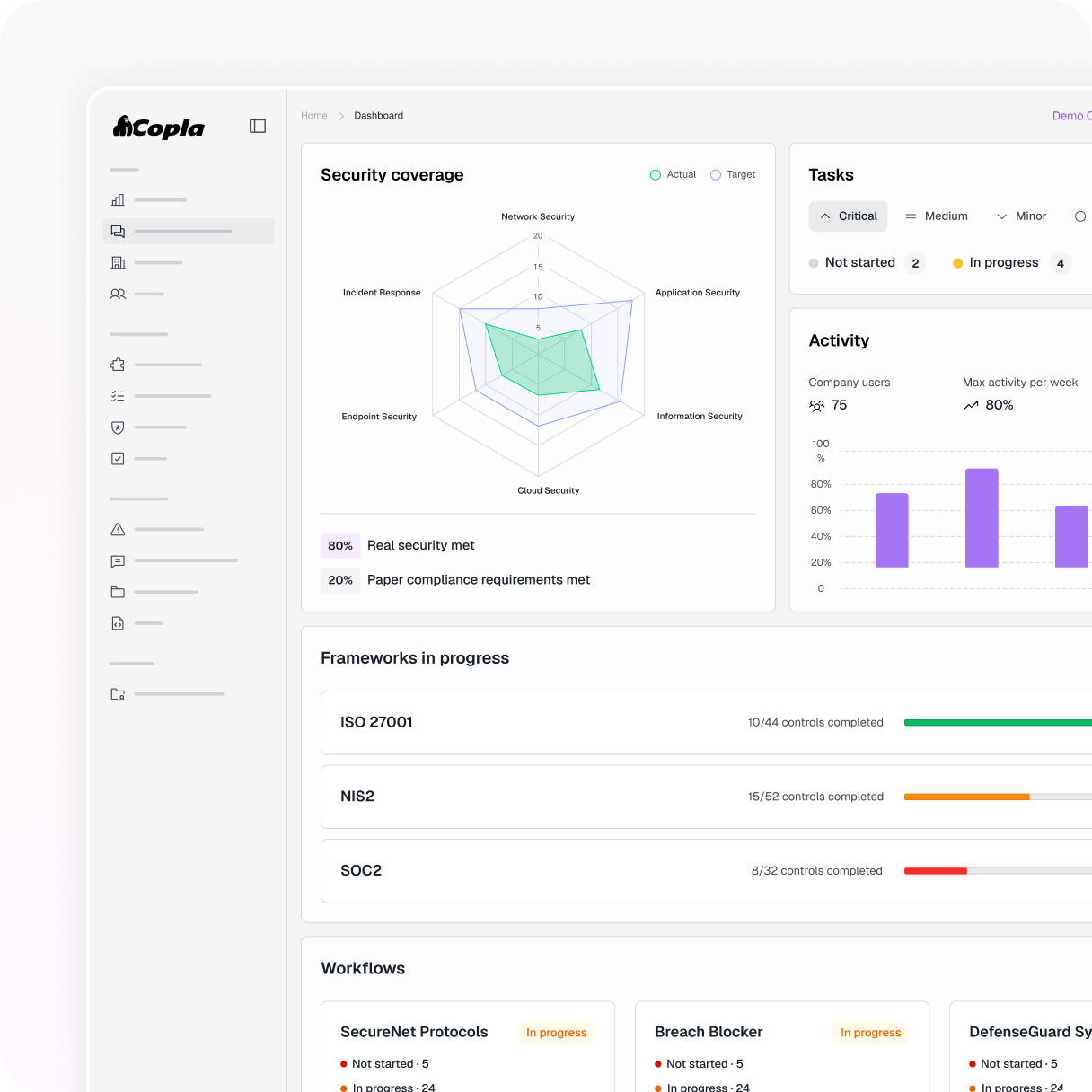
Framework-aligned scans & reporting
Coverage where attackers look
Managed by experts, not your engineers
Tie-in to the compliance platform
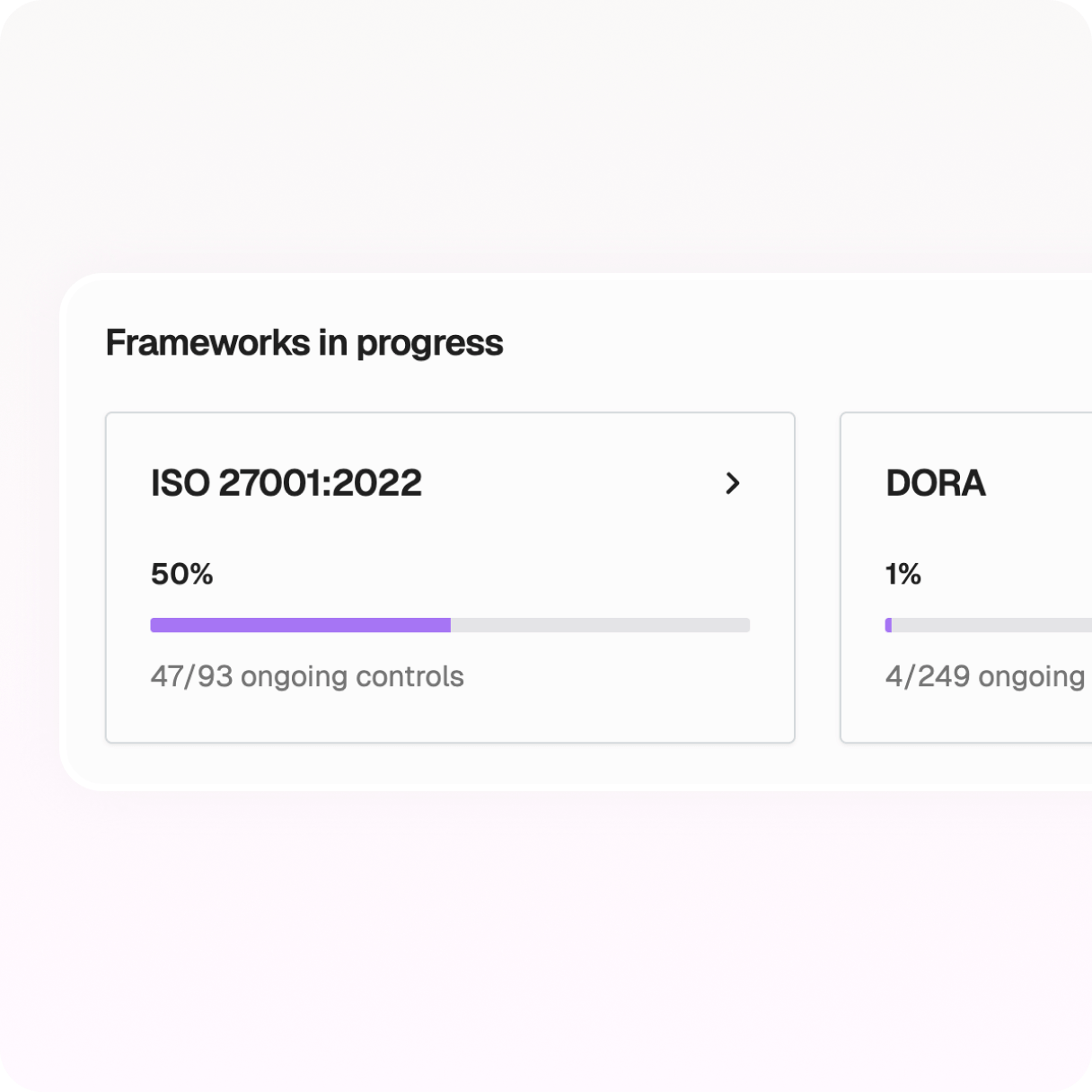
Done-for-you operating model (80%)
Framework-aligned scans & reporting

Coverage where attackers look

Managed by experts, not your engineers

Tie-in to the compliance platform

Done-for-you operating model (80%)

— FMpay
— Swotzy
— Axiology

Expertise and delivery



No—pentesting is a separate (complementary) service. We can bundle or sequence them for maximum value.
Choose raw tool outputs or tailored reports with control mapping—both come with remediation notes.
Yes—quarterly scans are available; we’ll align cadence to risk and regulatory needs.
Minimal: define scope, access, and targets—we handle the rest and return prioritized results.