Expert-led penetration tests that map vulnerabilities, validate real-world impact, and give you clear, prioritized fixes.

Top-rated on G2 — thanks to our customers.







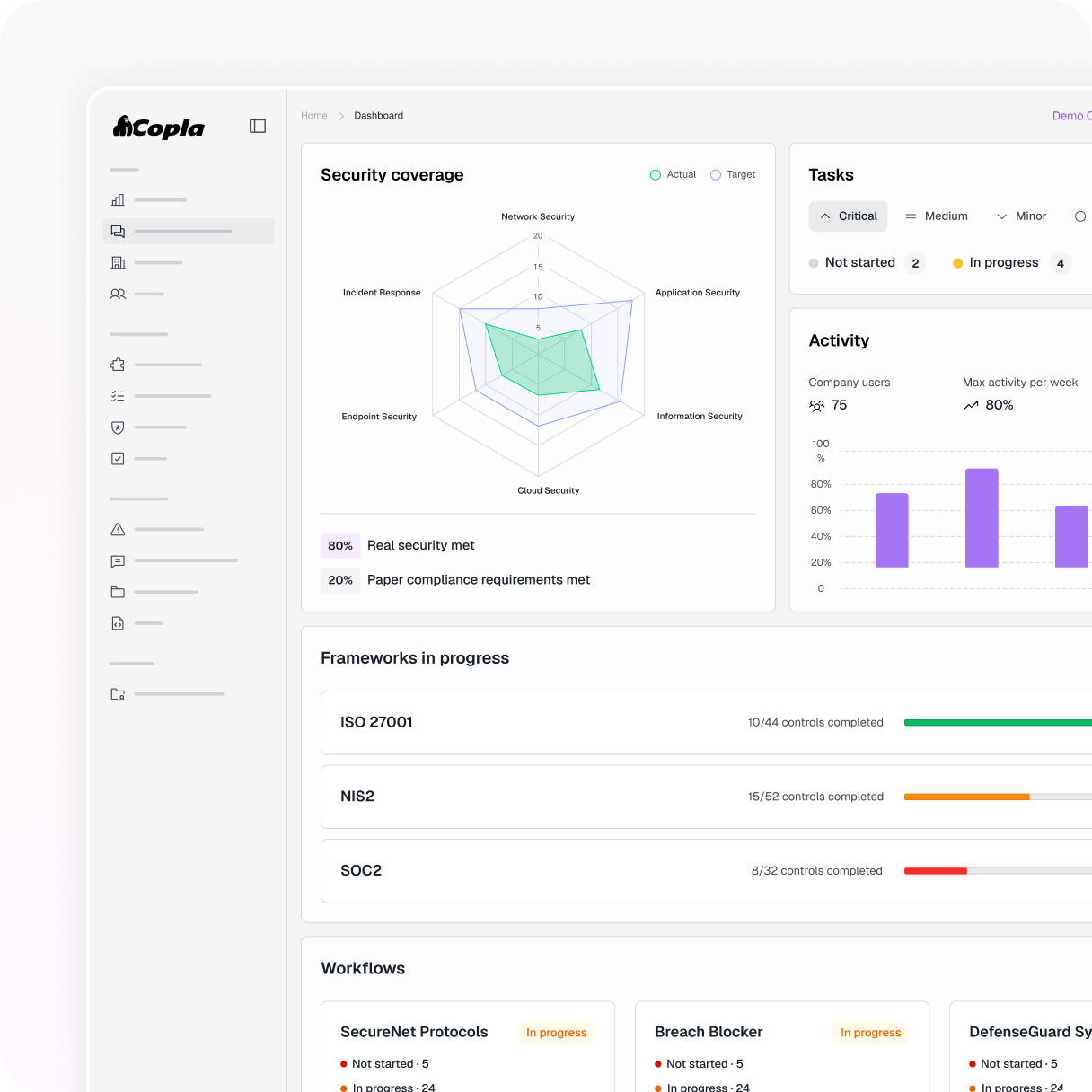
Gain a clear understanding of your environment with focused data collection.
Safely exploit vulnerabilities to confirm which risks actually matter.
Translate technical findings into what truly affects your organization.
Get prioritized fixes and CISO-level support to close gaps quickly—without guesswork or noise.
Real attacks, real answers
Realistic attack simulation & exploitation
Post-exploitation impact assessment
Executive-ready reporting
Demonstrable due diligence
Done-for-you operating model (80%)
Real attacks, real answers
Realistic attack simulation & exploitation

Post-exploitation impact assessment

Executive-ready reporting

Demonstrable due diligence

Done-for-you operating model (80%)

— FMpay
— Swotzy
— Axiology

Expertise and delivery



Targeted data gathering, vulnerability identification, safe exploitation, post-exploitation impact assessment, and a detailed remediation report—plus hands-on support.
Web applications, networks, cloud infrastructures, and internal systems.
They include prioritized findings, business impact, and step-by-step recommendations your teams can execute immediately.
Yes—our experienced CISOs provide personalized guidance through remediation and re-testing.