A structured, online system—built from CISO-created templates—that guides your team to capture the right facts, keeps them current, and turns data into action across vendors, assets, DORA obligations, and more.

Top-rated on G2 — thanks to our customers.







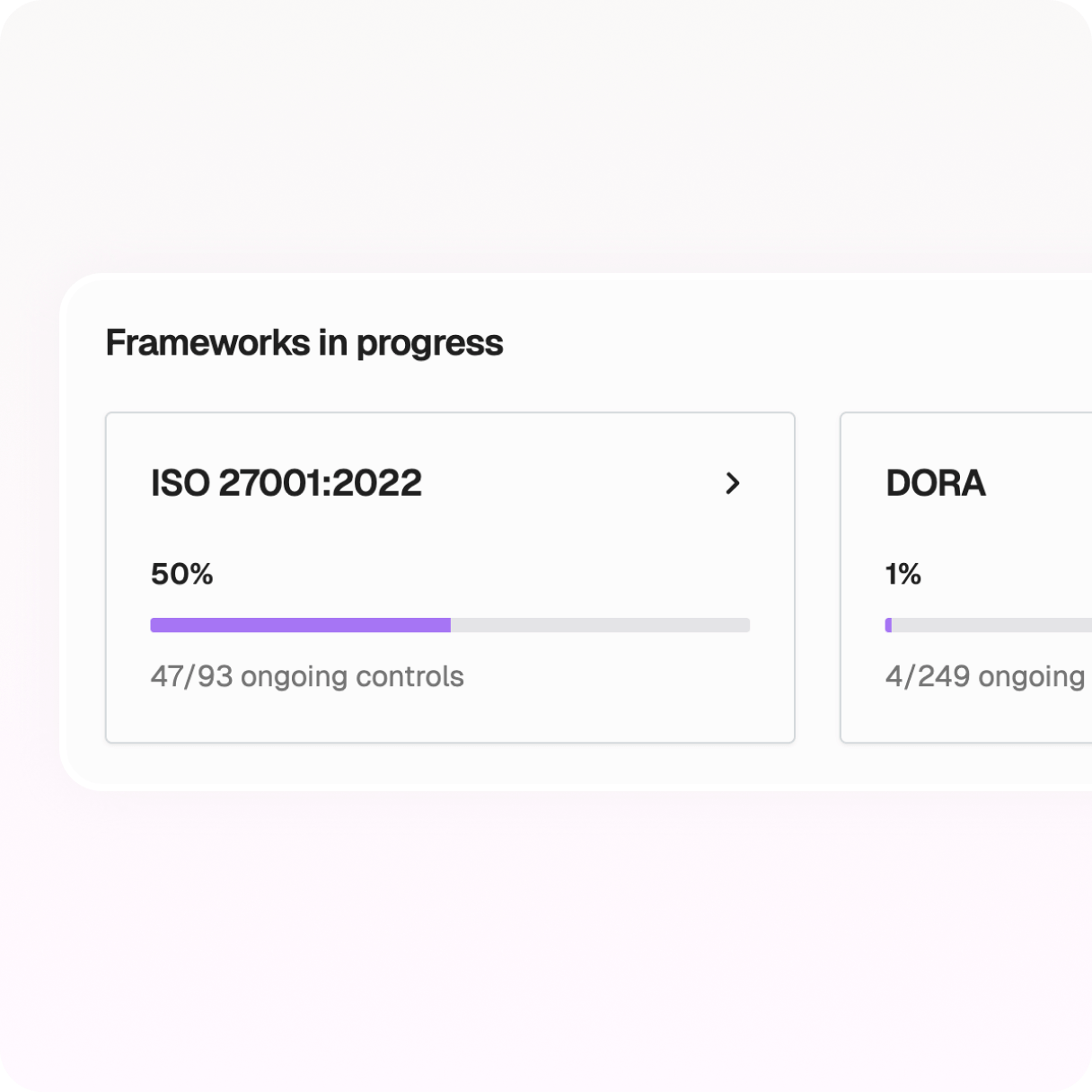
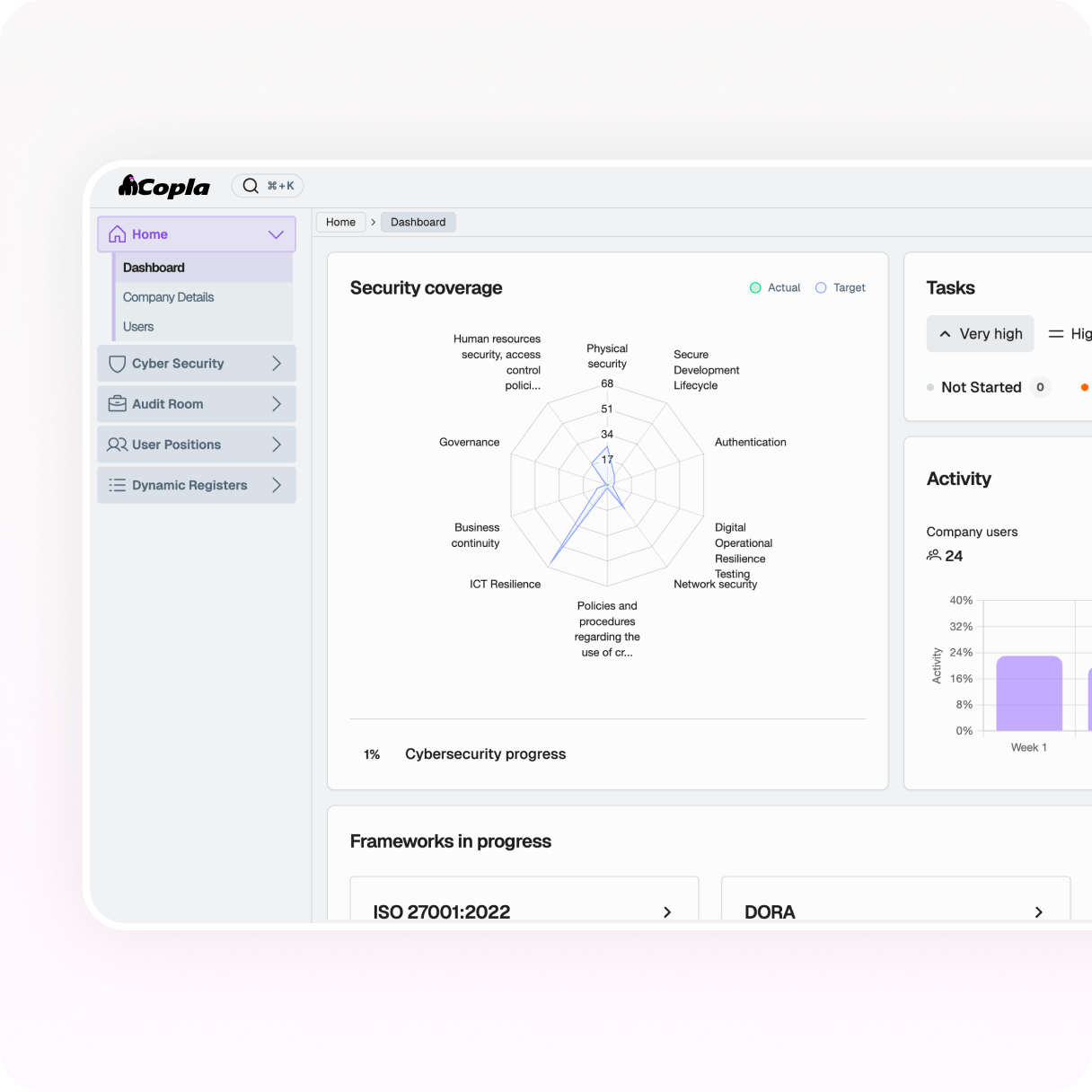
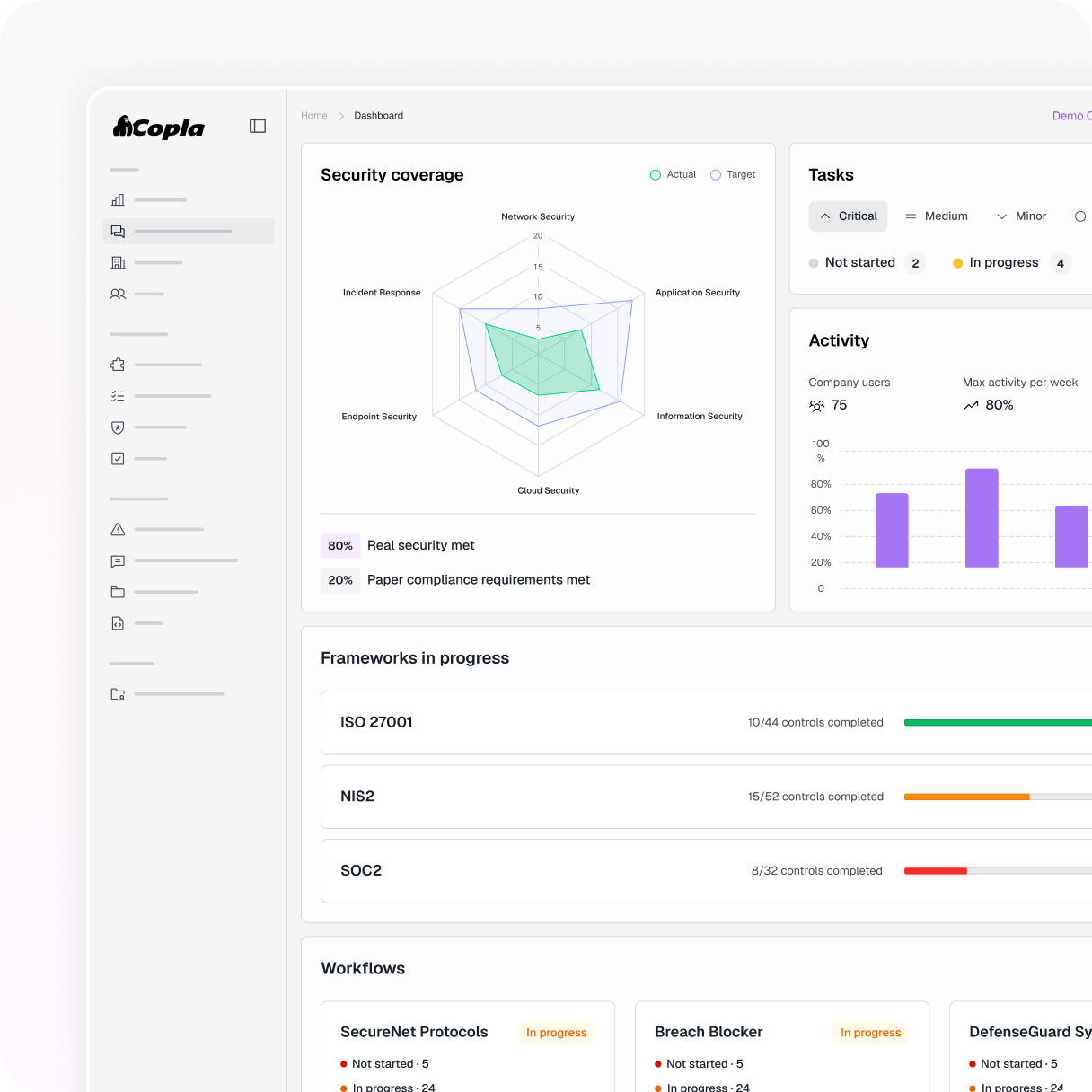
Organize vendors, assets, DORA records, and more using CISO-designed templates.
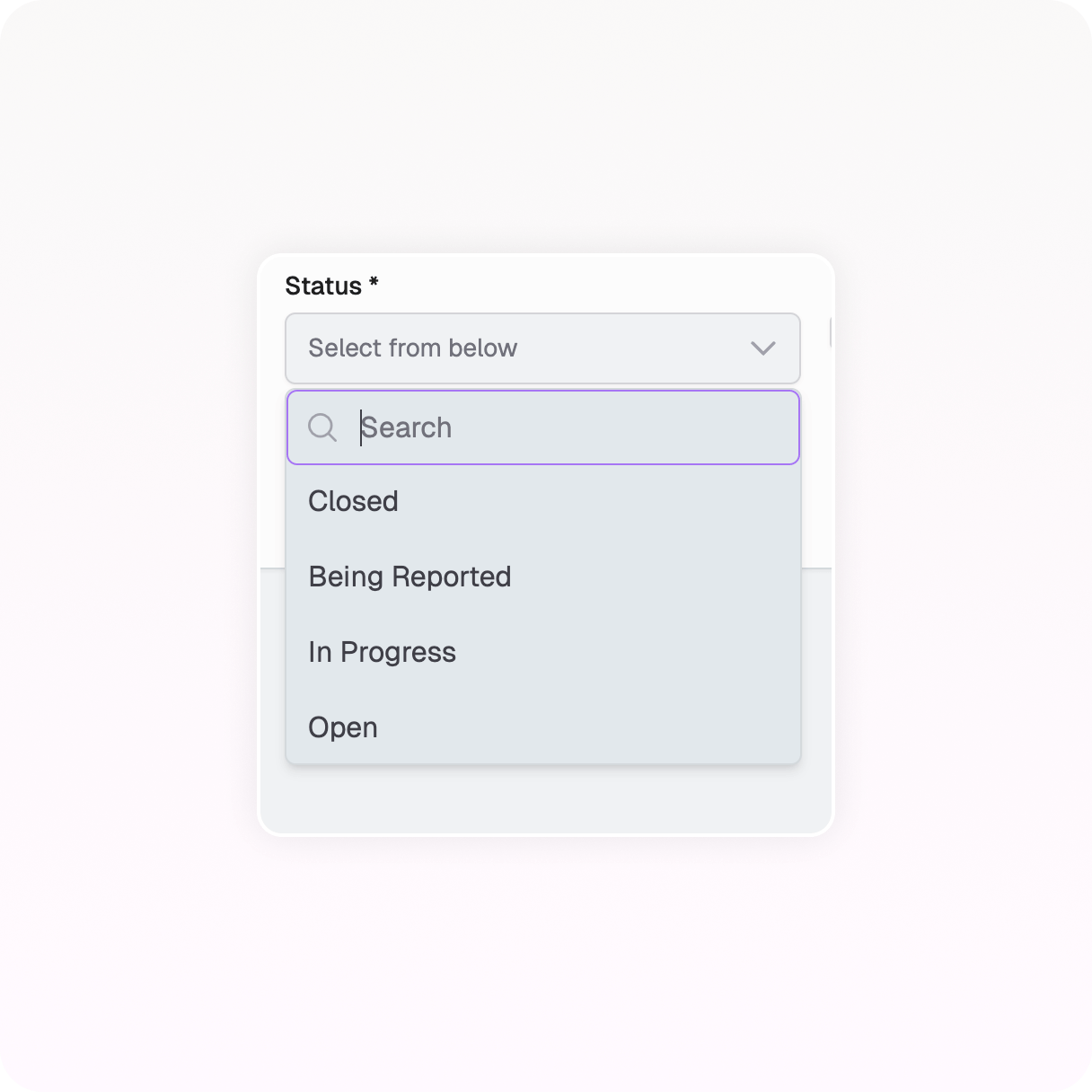
Complete forms with independent team input or CISO support for structured data collection.
Create tailored registers and store data once for access across all compliance activities.
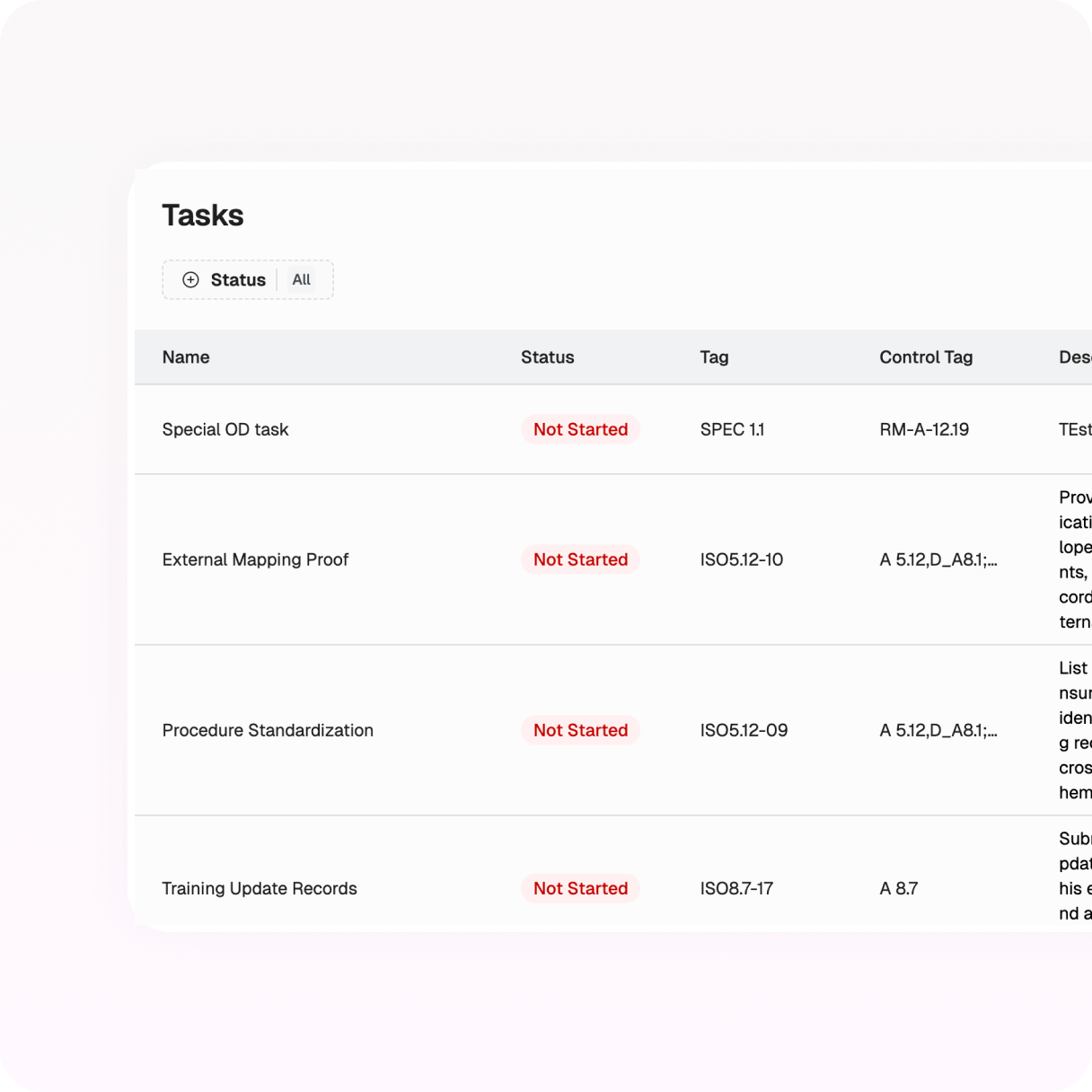
Trigger actions and collect missing evidence automatically to stay audit-ready.
From education to evidence
CISO-authored templates for every essential register
Actionable governance
CISO-in-the-loop support
Task handoff from registers
Done-for-you operating model (80%)
From education to evidence
CISO-authored templates for every essential register

Actionable governance

CISO-in-the-loop support

Task handoff from registers

Done-for-you operating model (80%)

Centralize third-party relationships. Record, assess, and monitor vendor risks—simplifying due diligence and ensuring supplier compliance.
Map digital and physical assets—servers, endpoints, software, data flows—for a real-time view of what you have and what you must protect.
Create your own registers for anything unique to your program—same guided forms, governance, and evidence workflows.

Guide your organization through Article 17 requirements: document ICT third-party contracts, capture risk assessments, and align entries with supervisory expectations.
— FMpay
— Swotzy
— Axiology

Expertise and delivery



They’re standardized, governed, and actionable—guided forms, ownership, audit trails, and workflows turn data into work and evidence.
Yes—start from CISO templates and adapt fields, picklists, and ownership to fit your environment.
Owners are assigned per register or entry; scheduled reviews and attestations keep data current.
CISOs (or the system) can trigger actions or workflows that request precisely what’s missing—artifacts, approvals, or updates.