When the Digital Operational Resilience Act (DORA) was first announced, many teams treated it like yet another item on the already crowded “EU regulation” bingo card. The mood changed around the time serious gap analyses started landing on executives’ desks and people realized: this is not just another cybersecurity guideline.
As of January 17, 2025, the directive is fully applicable and has become the backbone of EU-wide digital resilience for financial services.
DORA rewires how you think about ICT risk, third-party dependencies, and incident response. It also drags your entire digital ecosystem into the spotlight—cloud providers, fintech partners, security vendors, and anyone else keeping your systems alive at 3 a.m.
In this article, I want to walk you through what DORA banking regulation really means for financial services, why many organizations are struggling with implementation, and how to treat DORA compliance in finance as an operating model instead of a one-off project.
DORA As A System Upgrade For Financial Services
DORA is not another sidecar framework. It is a single, horizontal regulation covering how EU financial entities manage ICT risk, test resilience, report incidents, and control third-party dependencies.
Instead of scattered rules across sector-specific laws, DORA finance regulation brings everything under one roof for almost the entire financial sector.
It applies to more than 20 types of financial entities, plus ICT third-party service providers, including those designated as “critical” by EU authorities.
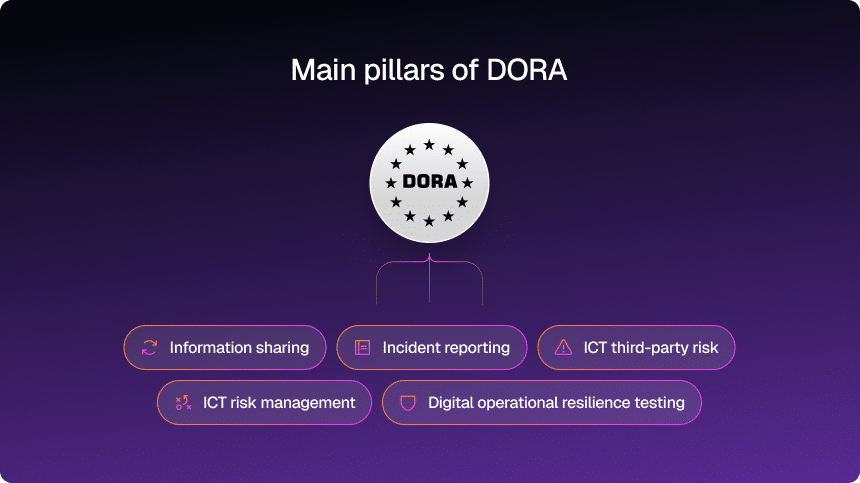
Here is what sits at the core of this framework:
- A formal ICT risk management framework embedded into overall risk governance (not a side PDF in the security folder).
- Harmonized rules for ICT-related incident management, classification, and reporting, supported by detailed technical standards adopted in 2024.
- A structured digital operational resilience testing program, including advanced threat-led penetration testing (TLPT) for certain entities.
- A robust regime for managing ICT third-party risk, plus an EU-level oversight framework for “critical” ICT providers such as major cloud platforms.
So when people talk about “DORA financial services,” they’re really talking about this full package: governance, testing, reporting, third-party control, and information sharing, all wired into how your business works day to day.
In practice, this means DORA is less about having “a security policy” and more about proving that digital resilience is part of your operating system.
Who DORA Actually Hits (Spoiler: It Is Not Just Banks)
One of the reasons DORA compliance in finance feels overwhelming is its scope. This is not a banking-only story. The regulation intentionally wraps almost the entire financial value chain into one resilience standard.
| Category | Examples of entities |
| Banks & credit institutions | Commercial banks, savings banks, credit unions, and investment banks |
| Insurance & reinsurance | Life insurers, non-life insurers, and reinsurance firms |
| Investment firms | Asset managers, hedge funds, private equity firms |
| Payment & e-money institutions | Payment processors, digital wallets, e-money providers |
| Trading & market infrastructure | Stock exchanges, central securities depositories, clearing houses |
| Crypto-asset service providers (CASPs) | Cryptocurrency exchanges, custodians, wallet providers |
| Third-party ICT service providers | Cloud computing firms, cybersecurity providers, data centers |
| Other financial entities | Credit rating agencies, auditors, and pension funds |
Under DORA, you may be a supervised ICT third-party, and if you are big enough or important enough, you may be formally designated “critical” and fall under direct oversight by the European Supervisory Authorities.
PRO TIP
Even if your organization is not headquartered in the EU, DORA may still apply if you serve EU-based clients or partner with in-scope financial entities. Conduct a jurisdictional impact analysis to determine your regulatory obligations early.
Why DORA Compliance In Finance Feels So Hard
Most institutions did not start from zero. They already had ISO 27001 initiatives, local ICT guidelines, maybe NIS2 workstreams running in parallel. Then DORA showed up and said: great start — but now harmonize, evidence, and scale all of it.
A few pressure points keep coming up in conversations with CISOs, CTOs, and compliance heads.
Don’t know if you’re DORA-compliant?
We’ve created a free tool to assess your organization’s DORA readiness in just minutes. Get your compliance score and find gaps now, before auditors do.
Governance And Accountability: Security As A Board Topic
Here’s the thing about DORA: it wants boards and executives to own ICT risk, not just nod through an annual security presentation. Senior management must approve the ICT risk management framework, regularly review risk exposure, and be able to explain decisions to supervisors.
That means:
- Clear roles and responsibilities for ICT risk across the first and second lines of defense.
- Regular, structured reporting to the management body on vulnerabilities, incidents, and third-party dependencies.
- Documented risk appetite for ICT risks—not just “low, medium, high” labels tucked away in a policy.
If your governance model still looks like “IT handles security, compliance handles paperwork,” DORA will expose that gap quickly.
Testing Requirements: From Annual Pen Test To Continuous Proof
Under DORA, you are expected to maintain a risk-based testing program that covers your ICT tools, systems, and processes at least annually and, for many entities, includes advanced testing based on threat-led penetration testing (TLPT) at least every three years.
TLPT is not just a fancy pen test. It:
- Simulates realistic attack scenarios using current threat intelligence.
- Runs on live production systems supporting critical or important functions.
- Follows detailed regulatory technical standards that align closely with frameworks like TIBER-EU.
This is where many organizations realize they do not just have a tooling problem; they have a coordination problem. Running TLPT every three years, on top of ongoing testing, requires planning, budget, vendor management, and board-level visibility.
PRO TIP
Time your first TLPT (threat-led penetration test) early in your compliance cycle to identify blind spots. Use the results to refine your incident response playbooks and demonstrate maturity during regulatory inspections.
Third-Party Risk: Your Cloud Is Now A Regulatory Topic
DORA treats ICT third-party risk as a first-class regulatory concern. You must:
- Know which providers support critical or important functions.
- Assess them before onboarding and throughout the relationship.
- Embed DORA-aligned clauses into contracts (e.g., on audit rights, sub-outsourcing, incident reporting, and exit strategies).
On top of that, critical ICT providers can now be designated and directly supervised by EU-level authorities. This has already started for major cloud and tech providers.
If your current vendor management is still spreadsheet-driven and purely commercial, DORA will feel like a shock.
Incident Reporting And Response: Deadlines Get Real
Under DORA and its implementing standards, major ICT-related incidents and significant cyber threats must be classified and reported within defined timelines using harmonized templates.
That implies:
- A clear internal playbook for detecting, triaging, and classifying incidents.
- Integration between security operations, risk, and compliance so that reporting can happen fast without chaos.
- Post-incident reviews feed back into your risk management and testing programs.
The short version: if you still treat compliance as a “paper exercise,” DORA will very quickly turn into a fire drill.
Your First 12–18 Months Under DORA: What To Actually Do
With DORA now fully applicable, the question is not “are we aware of this regulation?” but “how fast can we close the remaining gaps without burning out our teams?”
| Action item | Purpose |
|---|---|
| Conduct a structured gap analysis | Identify where your current ICT risk, testing, and vendor practices fall short under DORA. |
| Establish board-level oversight | Make ICT risk and resilience a standing agenda item with clear accountability. |
| Implement continuous monitoring | Use tooling to track vulnerabilities, incidents, and control status in near real time. |
| Strengthen third-party risk management | Classify critical providers, update contracts, and formalize assessment cycles. |
| Plan TLPT and scenario testing | Build a multi-year testing roadmap aligned with Article 24–26 and local supervisor guidance. |
One practical move I strongly recommend: create a cross-functional DORA steering group. Legal, compliance, IT, security, operations, and business all at the same table. When everyone owns a slice, translation from regulatory text to day-to-day process becomes much easier.
And when you schedule your first TLPT, do it early in your cycle. The findings will sting, but they also give you a concrete, risk-based story to tell regulators about how you are improving.
Resilience As Strategy, Not Just Survival
DORA is not another regulatory hurdle to jump and forget. It is a structural reset for how digital finance is supposed to survive disruption—whether that is a cyberattack, provider outage, or an ugly combination of both.
The real question for leadership is no longer “can we comply?” It is:
Are we willing to treat DORA as the baseline for how we design, test, and run our business—not just our IT?
Why Copla Is the Smart Way to Do DORA Compliance
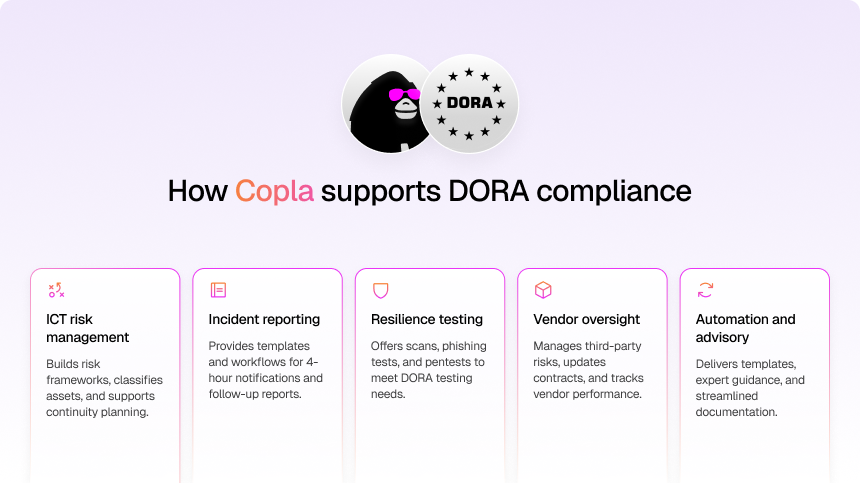
Copla is built for teams that want DORA compliance without burning out their staff or their budget. By pairing an automation-first platform with expert CISOs, Copla delivers 4 main advantages:
- Helps to reduce compliance workload by up to 80%
- Automates key DORA compliance tasks
- Guides you through the compliance process step-by-step
- Provides CISO-level leadership without the overhead
On top of that, clients typically save over €60K per year compared to hiring in-house staff to handle the same compliance workload, while staying continuously audit-ready.
The only DORA compliance management platform you’ll need
Copla brings together capabilities such as asset and risk registries, evidence mapping, audit verification, regulatory reporting, vulnerability management, awareness training, and incident tracking — all in one place.
FAQ
-
What is the DORA regulation in banking and finance? +
The Digital Operational Resilience Act (DORA) is an EU regulation that sets unified rules for how financial entities manage ICT risk, test resilience, handle cyber incidents, and oversee critical third-party providers to ensure uninterrupted, secure delivery of financial services.
-
Who must comply with DORA in the financial sector? +
Banks, insurers, investment firms, payment and e-money institutions, market infrastructures, crypto-asset service providers, pension funds, and most ICT third-party providers serving them (especially critical cloud/tech providers) must comply if they operate in, or serve clients in, the EU.
-
How is DORA different from existing banking regulations like PSD2 or CRD? +
PSD2 and CRD mainly address payments, prudential rules, and capital/risk at a financial level. DORA focuses specifically on digital operational resilience: ICT risk governance, incident reporting, testing, and third-party ICT oversight, creating one horizontal framework across the entire EU financial sector.
-
What happens if a financial firm is non-compliant with DORA? +
Supervisors can impose remediation orders, restrictions on activities, public censure, and significant administrative fines. Persistent non-compliance may trigger deeper supervisory measures, impact licensing and reputation, and complicate relationships with counterparties, investors, and critical ICT providers.