If getting compliant with the Digital Operational Resilience Act (DORA) feels a bit like trying to steer a ship through choppy waters, you’re definitely not the only one.
I’m here to help you navigate it with a bit more clarity. One of the biggest questions I hear is: “How do we get DORA certified?” or “How can we do it quickly?” The short answer: you can’t, because there actually is no official DORA certification program. Not for companies, and not for individual professionals.
But that doesn’t mean you’re off the hook — or that certifications don’t matter. In fact, it really helps to think of “compliance” as a kind of “certification” you need to pass every audit season.
In this guide, we’ll break down what being “certified” really means under DORA, why there’s no such thing as a formal “DORA certificate,” and how you can use existing, well-known certifications to support and demonstrate your alignment with the regulation’s requirements.
Made For Financial Institutions
Copla Registry
Spreadsheets make auditors think you don’t know what you’re doing. Prove compliance with the DORA ICT Register 5x faster.
Understanding DORA’s framework – what you’re really signing up for
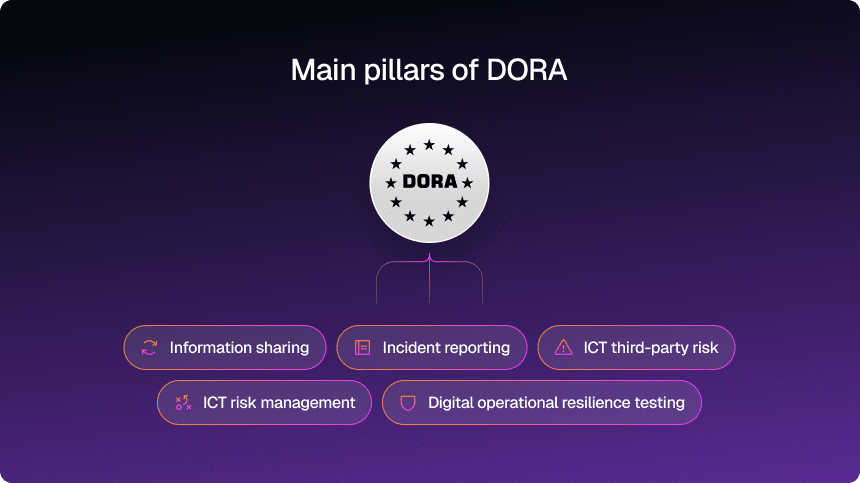
Let’s skip the legal mumble. The DORA regulation certification isn’t about paperwork. Actually, it’s about proving you’re ready to operate through cyber disruptions without panic.
At its core, the DORA Act certification model — or simply “compliance”— rests on five pillars that every financial firm and critical ICT vendor must tackle:
- ICT risk management – You need real policies, controls, and accountability to identify and manage tech-related risks.
- Incident reporting – Spot the threat, classify it fast, and notify regulators. You’ve got deadlines, so no guesswork allowed.
- Resilience testing – You’re expected to test your ability to withstand attacks. That means simulations, red-team drills, the works.
- Third-party risk management – DORA doesn’t stop at your firewall. Your cloud, software, and data providers need to meet resilience standards too.
- Information sharing – Regulators encourage secure sharing of threat intelligence to make the ecosystem more resilient.
Together, these build the foundation for a complete DORA framework certification strategy. If you’re not actively addressing all five, you’re not really in the compliance game yet.
PRO TIP
Build a “DORA Control Map” in a spreadsheet or GRC tool that lists each core DORA requirement alongside the exact ISO 27001 clauses or other framework controls you already have in place. Or use Copla platform, which does this automatically.
Why there’s no official “DORA certification”— and what that means for you
Here’s where it gets interesting. Despite the search spikes for DORA certification online, no EU body issues an official credential. That’s right: no shiny PDF or gold seal that declares “DORA Certified.”
But that doesn’t mean you’re off the hook. DORA compliance is all about demonstrating that your policies, processes, and controls align with the regulation and that they work under pressure. No matter how you call it, auditors will be looking for evidence.
So what should your DORA certification requirements checklist include?
- A mapped alignment between the DORA Act certification pillars and your current security frameworks
- Active, ongoing testing (not just a pen test once a year)
- Incident logs, resilience simulations, vendor audit records
- Internal training programs to ensure everyone knows their role
If you’ve got this evidence at hand and can tie it to standards like ISO/IEC 27001 or SOC 2, you’re effectively building a living, breathing DORA regulation certification profile.
Don’t know if you’re DORA-compliant?
We’ve created a free tool to assess your organization’s DORA readiness in just minutes. Get your compliance score and find gaps now, before auditors do.
Existing certifications that align with DORA requirements
If you’re looking to build a rock-solid compliance story, start by anchoring to existing frameworks.
These aren’t just “nice to have”. In fact, they’re how you operationalize DORA:
| Certification/Framework | What it covers | Role in DORA framework certification |
| ISO/IEC 27001 | Information Security Management System (ISMS) | Aligns directly with DORA’s ICT risk management and governance controls |
| ISAE 3402 / SOC 2 | Controls over data security, availability, and integrity | Vital for meeting DORA’s third-party and outsourcing oversight requirements |
| TIBER-EU / CBEST | Threat-led penetration testing in real-world conditions | Fulfills DORA’s resilience testing obligations |
| ISO/IEC 27017 / 27018, C5 (Germany) | Cloud security and data privacy certifications | Useful for DORA Act certification strategies involving cloud and SaaS ecosystems |
Instead of reinventing the wheel, use these certifications to build your DORA control matrix. It’s a practical way to show compliance without needing a new DORA metrics certification from scratch.
PRO TIP
Create a “Certification-to-DORA” matrix that maps each vendor or internal domain (e.g., ICT risk management, resilience testing) to the certification framework you’re using (ISO 27001, SOC 2, TIBER-EU, etc.). Use this living document in your vendors’ quarterly reviews to ensure continuous alignment. By the way, Copla does this on autopilot.
Training: building your team’s compliance muscle
If your team doesn’t speak “DORA” yet, now’s the time to teach them. It’s not optional. DORA’s requirements demands specialized knowledge, making DORA training an essential step for financial professionals and compliance officers
You can look for DORA certification online training options that break down the regulation in terms your ops, legal, and tech people can all get behind.
When selecting a course, check if it:
- Covers the five DORA pillars in depth
- Links to widely adopted frameworks (ISO, SOC 2, NIST, etc.)
- Offers a credential or certificate of completion (or any other evidence works as welll)
- Allows a pilot run before full enrollment
PRO TIP
DORA does expect your staff to be trained, but they don’t all need to become certified DORA gurus. Instead, give them short, chat-based awareness training, log who’s completed it, and document their scores. Done and dusted.
Those who are building their own training programs should note that DORA overlaps with other frameworks. Here’s a quick illustration:
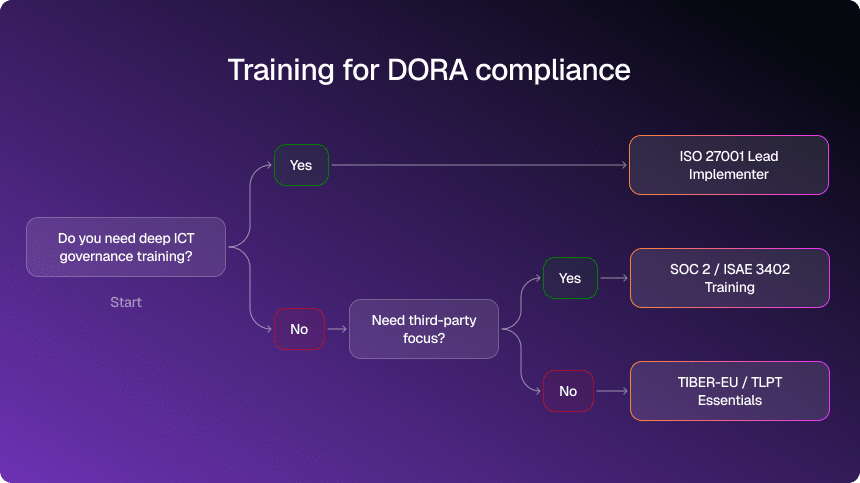
The real role of auditors — and why they matter more than ever
Even without a formal DORA auditor certification, regulators will expect third-party or internal assessors to evaluate your operational resilience practices. So what will auditors look for?
- A documented, working ICT risk management system
- Incident response records, timelines, and proof of regulator notification
- Simulation results from resilience testing
- Third-party vendor registers, oversight policies, and contracts
- Governance alignment across risk, compliance, and IT teams
Auditors with credentials like ISO/IEC 27001 Lead Auditor or CISA already meet the unofficial DORA auditor certification standard. You want people who can challenge your assumptions, not just nod and tick boxes.
PRO TIP
Host a mock audit workshop six months before your first DORA review. Use ISO 27001 Lead Auditor or CISA–qualified internal or external experts to simulate regulator questions on incident reporting, resilience testing, and third-party oversight—so you can close any compliance gaps well in advance.
So how do you become “audit ready” without a certificate?
Let’s be real: just because there’s no DORA certification body doesn’t mean you can wing it. Regulators will expect documentation, repeatable controls, and clear alignment with the regulation.
What matters is this:
- You’ve mapped each DORA requirement to an existing control, framework, or evidence
- You’ve got evidence of activity (not just intent)
- Your vendors are accountable and continuously assessed
- You run simulations and drills, not just annual reports
- You’ve trained your people, reviewed your gaps, and remediated weak spots
That’s what a strong DORA framework certification posture looks like, even if it’s not printed on fancy paper.
Why Copla Is the Smart Way to Do DORA Compliance
Copla is built for teams that want DORA compliance without burning out their staff or their budget. By pairing an automation-first platform with expert CISOs, Copla delivers 4 main advantages:
- Helps to reduce compliance workload by up to 80%
- Automates key DORA compliance tasks
- Guides you through the compliance process step-by-step
- Provides CISO-level leadership without the overhead
On top of that, clients typically save over €60K per year compared to hiring in-house staff to handle the same compliance workload, while staying continuously audit-ready.
The only DORA compliance management platform you’ll need
Copla brings together capabilities such as asset and risk registries, evidence mapping, audit verification, regulatory reporting, vulnerability management, awareness training, and incident tracking — all in one place.
FAQ
-
What is DORA certification? +
DORA certification isn’t a formal credential. It refers to the process of aligning your operations with the requirements of the Digital Operational Resilience Act (DORA) and demonstrating compliance through recognized security frameworks and internal controls.
-
Who needs to be compliant with DORA? +
All regulated financial entities in the EU, including banks, insurers, investment firms, and critical ICT third-party providers, must comply with DORA by January 17, 2025.
-
Is there a certification body for DORA? +
No official DORA certification body exists. Instead, organizations demonstrate compliance by aligning with standards like ISO 27001, SOC 2, TIBER-EU, and using those to satisfy DORA certification requirements.
-
What are the main pillars of DORA compliance? +
The five key pillars are: ICT risk management, incident reporting, resilience testing, third-party risk management, and information sharing.
-
What are the penalties for non-compliance? +
DORA enables national regulators to impose financial penalties, operational restrictions, or even bans from certain activities for non-compliant entities. The stakes are high — both reputationally and financially.