If I had a euro for every company that says “we take security seriously,” I could probably fund another compliance startup. Let’s be honest, we’ve all seen it. The same annual penetration test, the same glossy certificate, the same belief that resilience lives in a binder somewhere.
Then along came DORA, the Digital Operational Resilience Act, and it politely said:
“Cute. Now show us.”
Welcome to DORA testing — Europe’s polite but firm way of asking the financial sector to stop play-acting cybersecurity and start proving it.
Why DORA testing actually matters
Forget the legal phrasing for a moment. DORA testing requirements basically say:
“You don’t get to call yourself resilient until you can survive your own disaster movie.”
The DORA testing framework isn’t about box-ticking — it’s about proof.
You’re expected to test resilience like a muscle: push it, stress it, break it a bit, then build it back stronger.
That means moving beyond the once-a-year penetration test. It means designing a DORA testing program that runs continuously — scanning for vulnerabilities, stress-testing vendors, running attack simulations, and tracking results week after week.
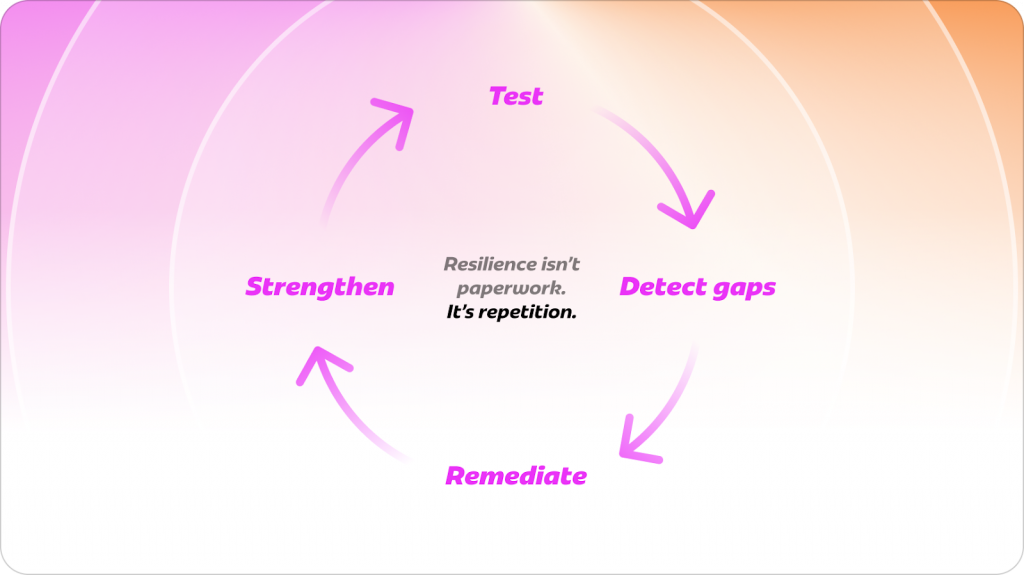
Resilience isn’t paperwork. It’s repetition.
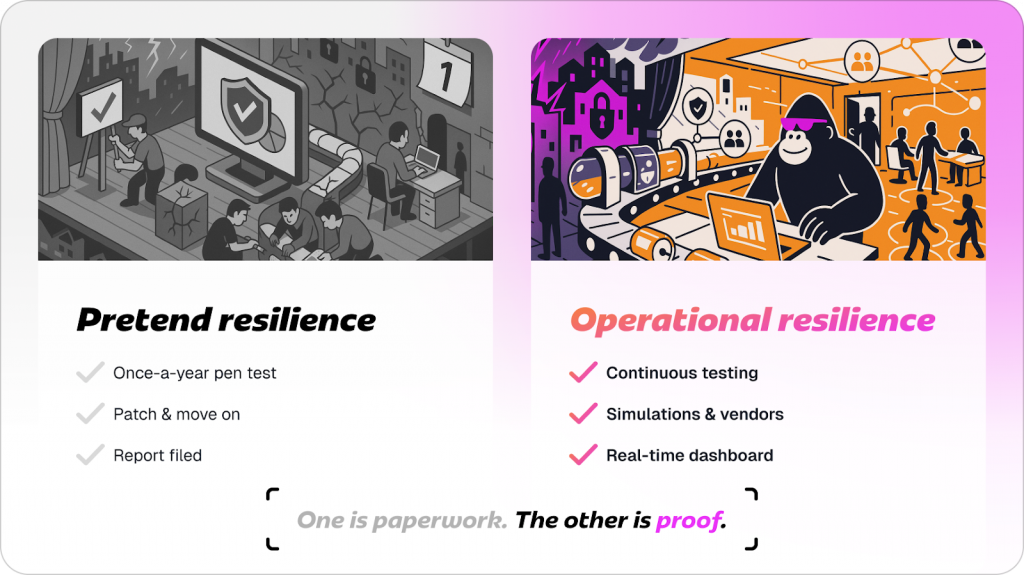
Testing versus pretending
Let me paint two very real pictures.
In the first, your IT team runs a pen test once a year, patches a few findings, writes a report, and moves on.
In the second, your DORA testing plan hums in the background all year long.
You’ve automated vulnerability testing.
You’ve run simulations with your partners.
You’ve trained people, not just systems.
When the regulator asks for evidence, you don’t panic; you just open your dashboard.
One version is theatre. The other is operational resilience. And DORA has made it clear which one it wants.
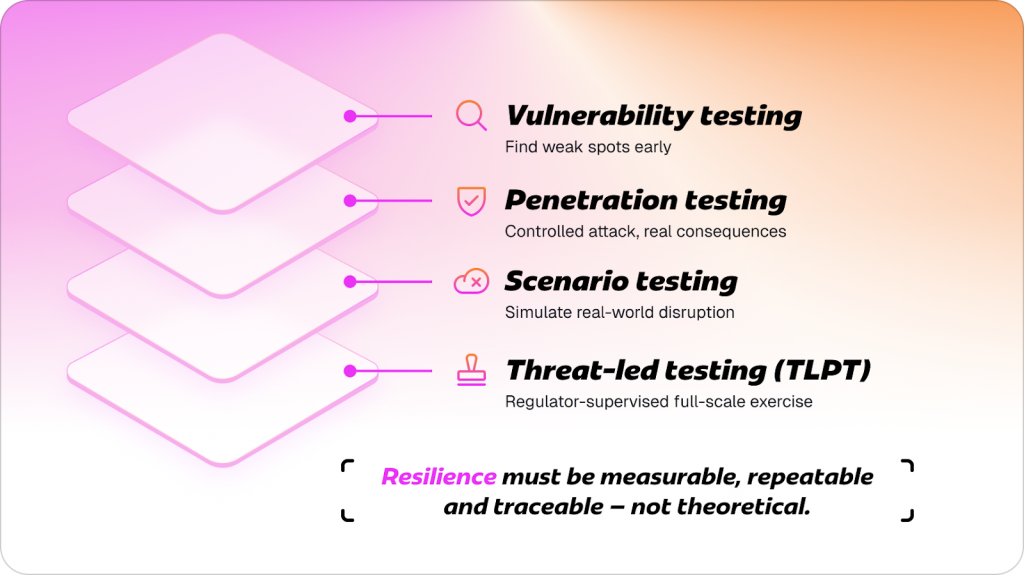
What’s actually inside a DORA testing framework
Here’s the backbone of every proper DORA testing program — minus the legalese:
- Vulnerability testing: find weak spots before someone else does.
- Penetration testing: controlled attacks, real consequences.
- Scenario testing: simulate realistic business disruptions, not just IT failures.
- Threat-led testing: full-scale, regulator-supervised red-team exercises for larger entities.
If that sounds exhausting, good. Real resilience isn’t built for comfort — it’s built for chaos.
Why DORA testing hurts (and why that’s progress)
DORA doesn’t care about your slide decks or slogans. It cares about whether you can take a punch and keep operating.
That’s the new standard. “Audit ready” is old news; “battle ready” is the goal.
It will hurt at first. Testing always does.
You’ll find gaps you didn’t know existed — in your systems, your processes, and occasionally your people.
But those discoveries are the point.
Every failed simulation, every clumsy drill, every awkward vendor call — that’s growth. That’s resilience culture forming in real time.
DORA penetration testing isn’t your old security audit
Traditional pen tests are like staged fights: you know when they’re coming, everyone plays along, and nothing changes.
DORA penetration testing raises the stakes. It’s not a compliance checkbox; it’s a regulatory expectation with teeth.
Every test must be risk-based, well-documented, and traceable. Regulators want to see evidence of:
- The method used
- The vulnerabilities found
- The fixes applied
- The follow-ups verified
They don’t just want proof you tested — they want proof you learned.
And remember, resilience doesn’t stop at your firewall. Your vendors, cloud providers, and partners are part of the same system. If they fail, you fail. That’s why DORA resilience testing forces you to test the whole ecosystem, not just your own backyard.
How real companies make DORA testing work
Here’s what separates companies that just comply from those that actually endure:
They stop waiting for auditors.
They automate evidence collection.
They make testing a habit, not a project.
They bring everyone into the process — compliance, IT, operations, even HR.
And they stop treating security as a mood.
When you run your DORA testing program continuously, testing stops being scary. It becomes normal.
The goal isn’t to show perfection — it’s to prove improvement.
If you’re still managing resilience testing in Excel, that’s not compliance. That’s archaeology.
The culture shock (and why it’s necessary)
When DORA landed, I called it GDPR’s muscular cousin.
It’s not about protecting privacy — it’s about protecting continuity.
It forces financial entities to own their operational resilience in a way no framework ever has.
Yes, it’s complex. Yes, it’s uncomfortable. But it’s also the clearest signal yet that resilience is a business function, not a side quest for IT.
DORA isn’t asking you to be perfect. It’s asking you to be honest — and to prove, through structured testing, that your organization can take a hit and keep going.
Final thought: DORA testing isn’t an exam
Here’s the mindset shift I want you to take away:
DORA testing is training, not testing.
You don’t do it once to get a certificate. You do it regularly to stay in shape.
The goal isn’t to pass. The goal is to endure.
Because resilience isn’t a document — it’s a discipline.