When it comes to DORA vs NIS2 the compliance reality is simple: it’s not “either/or”, it’s “both, at the same time”. Both of these frameworks are EU power tools for cybersecurity. Both want you more resilient, more structured, more accountable.
But they’re not twins.
DORA is your finance-sector drill sergeant.
NIS2 is your cross-industry safety inspector.
If you’re trying to build one strategy that covers both, you need to know where they overlap — and where they absolutely don’t. Let’s break it down without the legal mumble.
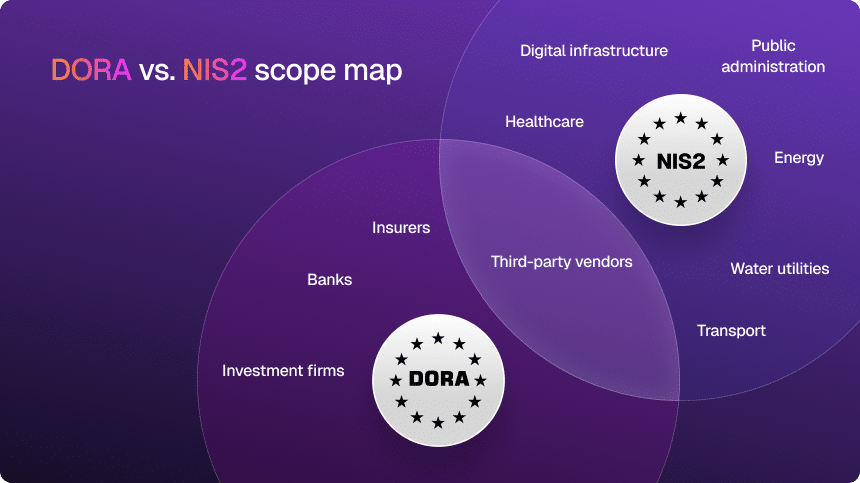
DORA vs NIS2: what they actually do
Think of it this way:
- DORA (Digital Operational Resilience Act) is about:
“Can your financial institution stay operational when your ICT goes sideways?” - NIS2 (Network and Information Security Directive 2) is about:
“Can essential services in Europe keep functioning when cyber chaos hits?”
Same theme (resilience), very different casts.
DORA in one sentence
A sector-specific regulation for the financial industry that forces banks, insurers, investment firms, and critical ICT providers to prove they can withstand, respond to, and recover from ICT incidents.
NIS2 in one sentence
A cross-sector directive that pulls critical and important entities (energy, health, transport, digital infrastructure, etc.) into a harmonized, baseline cybersecurity regime across the EU.
If you operate in financial services and fall under NIS2’s “essential/important entity” categories, congratulations: you’re playing on hard mode.
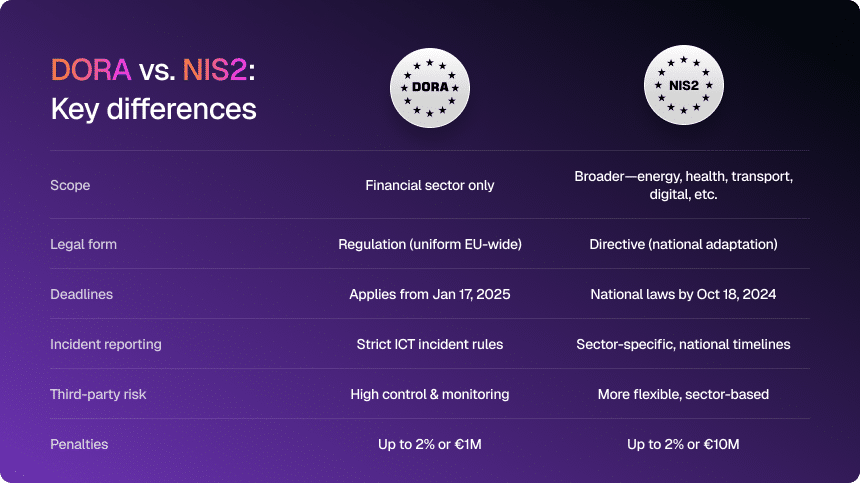
DORA vs NIS2 at a glance
Here’s the side-by-side compariosn, for a clearer picture of the two frameworks:
| Aspect | DORA | NIS2 |
| Scope | Financial sector only: banks, insurers, investment firms, critical ICT third parties | Many sectors: energy, health, transport, water, digital infrastructure, and more |
| Legal instrument | Regulation – directly applicable in all EU states, no local remixing | Directive – must be transposed into national law, so there’s room for country-level differences |
| Implementation deadline | Fully applicable from 17 January 2025 | Member states had to transpose by 18 October 2024; entities must comply with those national laws |
| Incident reporting | Strict, ICT-specific incident reporting with staged deadlines and detailed follow-up | Significant incidents reported under national rules (usually 24–72 hours), broader in scope |
| Third-party risk management | Heavy focus on ICT providers: contracts, oversight, monitoring, exit strategies | Strong emphasis on supply chain security, but more flexible and sector-dependent |
| Penalties for non-compliance | Up to 2% of global annual turnover or €1M for individuals | Up to €10M or 2% of global turnover, whichever is higher |
PRO TIP
Map your overlap. Draw a simple Venn diagram of which systems and processes in your organization fall under both DORA and NIS2. That way, you immediately spot areas where a single control update will satisfy both frameworks, cutting duplication.
By the way, Copla does this automatically.
Under the hood: how DORA and NIS2 think about “technical requirements”
Both frameworks say:
“You don’t get to call yourself resilient just because you bought a firewall and wrote a policy.”
But they come at it from different angles.
- DORA: “You’re handling financial stability. Your ICT resilience better be battle-tested.”
- NIS2: “You’re running essential services. You must hit a minimum level of cyber maturity — no excuses.”
Let’s unpack what that means in practice.
DORA’s technical mandates
DORA is not impressed by one-off projects. It wants continuous, structured ICT risk and resilience management across the financial ecosystem.
Here’s what it expects you to do — and be able to prove.
1. ICT risk management
You need a full risk framework for ICT:
- Identify vulnerabilities and critical assets
- Monitor threats and anomalous activity
- Define impact tolerances and continuity plans
- Link risks to controls, owners, and remediation timelines
If your risk register lives in a dusty spreadsheet, DORA will not be amused.
2. Incident reporting (with receipts)
Significant ICT incidents must be:
- Detected quickly
- Classified using clear severity criteria
- Reported within strict timelines (initial, interim, final)
- Documented with causes, impact, and fixes
“Something bad happened last week, but we’re still figuring it out” is not a reporting strategy.
3. Resilience testing (not just pen tests)
DORA expects you to prove your setups work under stress:
- Advanced penetration testing
- Scenario-based tests (business processes, not just tech)
- Regular, risk-based testing cycles
- Documented results and remediation tracking
If your only test is “we restore a backup once a year,” that’s not resilience. That’s wishful thinking.
4. Third-party risk management
DORA treats critical ICT providers as part of your core infrastructure:
- Explicit contractual requirements for security and resilience
- Ongoing performance and security monitoring
- Exit and substitution strategies
- Audits and assurance reports with teeth
If your vendor contract only says “will take appropriate security measures,” you already know that’s not going to cut it.
5. Information sharing
DORA nudges financial entities to share threat intelligence:
- With peers
- With authorities
- Through formal or sectoral sharing setups
Because learning quietly from your own incidents is fine. But learning from everyone’s incidents is resilience at scale.
Don’t know if you’re DORA-compliant?
We’ve created a free tool to assess your organization’s DORA readiness in just minutes. Get your compliance score and find gaps now, before auditors do.
NIS2’s technical mandates: raising the floor across Europe
NIS2 has a broader ambition: make sure essential and important entities aren’t one phishing email away from chaos.
Instead of ultra-specific sector mechanics, NIS2 sets a baseline of “good security hygiene” that everyone must meet, then lets sectors go further.
Here’s what that baseline looks like.
1. Cybersecurity risk management
Entities must:
- Perform risk assessments on networks and systems
- Implement proportionate technical and organizational controls
- Keep security aligned with the evolving threat landscape
This is your minimum operating standard, not your aspirational future state.
2. Incident reporting & response
NIS2 is serious about timely reporting:
- Significant incidents must be reported within strict time windows (typically 24–72 hours)
- Updates and final reports follow as the picture becomes clearer
- Authorities use this to coordinate broader response and oversight
No more “we’ll announce it when we’re ready.” The clock starts when you detect.
3. Supply chain security
NIS2 drags your vendors and partners into the conversation:
- Assess supplier security posture
- Build security expectations into contracts
- Monitor critical providers over time
- Treat supply chain as part of your own attack surface
If your onboarding checklist for suppliers says “Signed? Good” — time to upgrade it.
4. Security awareness & training
NIS2 doesn’t let you pretend your people are the problem and then stop there. It requires you to train them:
- Regular, role-specific awareness
- Practical exercises and refreshers
- Management involvement, not just IT preaching
Because “we sent a phishing e-learning video in 2019” is not a culture.
5. Cooperation & information exchange
NIS2 pushes for cross-border, cross-sector collaboration:
- National CSIRTs and competent authorities
- Entities sharing insights and trends
- Coordinated responses to larger incidents
No single entity gets to fight modern cyber threats alone — and NIS2 knows it.
What this all does to your security practice
Both laws are sending the same message:
“Compliance is not a folder. It’s how you run your business.”
If you’re under DORA (financial entities)
Prepare to:
- Upgrade ICT risk management from “documentation” to live system
- Run regular resilience testing that touches processes, tech, and people
- Build robust incident detection and reporting pipelines
- Put serious structure around vendor oversight
This usually means new tooling, new workflows, and frankly, some uncomfortable truths about your current state.
If you’re under NIS2 (essential & important entities)
Get ready to:
- Harden your basic cybersecurity posture (access, patching, logging, monitoring)
- Improve incident detection, response, and escalation discipline
- Treat your supply chain as part of your own threat surface
- Embed training and awareness into how you onboard and manage staff
In both cases, the old model — “once-a-year audit, panic in Q4, forget by Q1” — is dead.
PRO TIP
Executive dashboards drive buy-in. Surface your combined DORA/NIS2 metrics (incident counts, test completion, vendor-risk scores) on a single slide for your board. Seeing the big picture side-by-side cements funding for shared tools and reduces “audit fatigue.”
Why Copla Is the Smart Way to Do DORA and NIS2 Compliance
Copla is built for teams that want DORA and NIS2 compliance without burning out their staff or their budget. By pairing an automation-first platform with expert CISOs, Copla delivers 4 main advantages:
- Helps to reduce compliance workload by up to 80%
- Automates key DORA and NIS2 compliance tasks
- Guides you through the compliance process step-by-step
- Provides CISO-level leadership without the overhead
On top of that, clients typically save over €60K per year compared to hiring in-house staff to handle the same compliance workload, while staying continuously audit-ready.
The only compliance management platform you’ll need
Copla brings together capabilities such as asset and risk registries, evidence mapping, audit verification, regulatory reporting, vulnerability management, awareness training, and incident tracking — all in one place.
FAQ
-
What is the main difference between DORA and NIS2? +
DORA is a finance-specific regulation focused on digital operational resilience for financial entities and their ICT providers. NIS2 is a cross-sector directive setting baseline cybersecurity requirements for a wide range of essential and important entities across the EU.
-
Do DORA and NIS2 apply to the same organizations? +
Sometimes, but not always. Financial entities mainly fall under DORA, while many critical sectors fall under NIS2. Some organizations — like financial market infrastructures or critical ICT providers — may be in scope for both and must align with both frameworks.
-
Is DORA stricter than NIS2? +
DORA is generally more prescriptive for the financial sector, especially around ICT risk, testing, and third-party oversight. NIS2 is broader but sets strong minimum cybersecurity standards. For dual-scope entities, DORA usually feels stricter operationally, while NIS2 adds wider governance and supply chain pressure.
-
When do the regulations take effect? +
NIS2 had to be transposed into national laws by 18 October 2024, with organizations expected to comply under those local rules. DORA becomes fully applicable on 17 January 2025, giving financial entities a fixed EU-wide go-live date.