Not too long ago, many financial institutions treated cybersecurity like an IT chore. Patch Tuesday, annual pen test, maybe a policy refresh if someone remembered. Then ransomware, supply chain compromises, and cloud outages started hitting the headlines. That’s when regulators decided it’s time for… another regulation.
As a result, the Digital Operational Resilience Act (DORA) directive dropped, sending a pretty blunt message to the financial sector:
“You can’t be digitally fragile and systemically important at the same time.”
But here’s something interesting: DORA isn’t just like any other directive. It’s a hardline blueprint built around five pillars designed to see if you can actually take a hit and get back up.
If DORA is still news to you, don’t worry. In this article, I’ll bring you up to speed on the DORA implementation timeline and key milestones.
From IT Problem To Boardroom Risk: What DORA Really Changed
DORA is an EU regulation, which means it is directly applicable law, not a soft guideline you can negotiate with.
It entered into force in January 2023 and began applying on 17 January 2025, covering banks, insurers, payment institutions, investment firms, and a long list of other financial entities and ICT providers that support them.
The regulation takes everything you used to bucket under “IT stuff” and reframes it as business continuity, systemic stability, and supervisory priority.
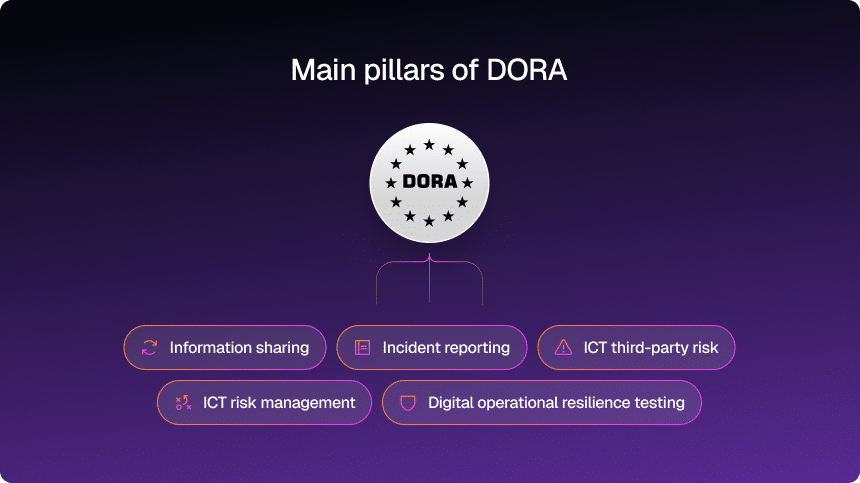
The five pillars it’s built on are not theory. They map directly to what regulators expect to see when they walk into your organization or open your documentation.
Here is how the core pillars translate into day-to-day reality.
| DORA Requirement/Pillar | Key expectation |
| ICT risk management | A documented, risk-based framework that identifies, assesses, mitigates, and tracks ICT risks. |
| Incident reporting | Defined thresholds, internal playbooks, and the ability to report major incidents on time. |
| Operational resilience testing | Regular, risk-based tests that go beyond checklists and actually stress your critical services. |
| Third-party risk management | Structured oversight of vendors, especially critical ICT third-party providers (CTPPs). |
| Information sharing | Participation in threat-intelligence and incident-sharing mechanisms, where relevant. |
When you put it all together, the shift is clear. DORA is not asking you to say you are resilient. It is asking you to prove it with governance, controls, testing, and evidence that tie back to these pillars.
If you treat this as “IT compliance,” you will constantly be behind. If you treat it as a core part of your operating model, it becomes much easier to make decisions, justify investments, and survive audits.
PRO TIP
Map controls to both DORA and existing frameworks. Create a single cross-reference matrix that aligns DORA’s five pillars with your ISO 27001, GDPR, or PCI-DSS controls — this lets you spot overlap, eliminate duplication, and optimize remediation efforts. By the way, Copla does this automatically.
The DORA Timeline: Not Just Dates, But Operational Checkpoints
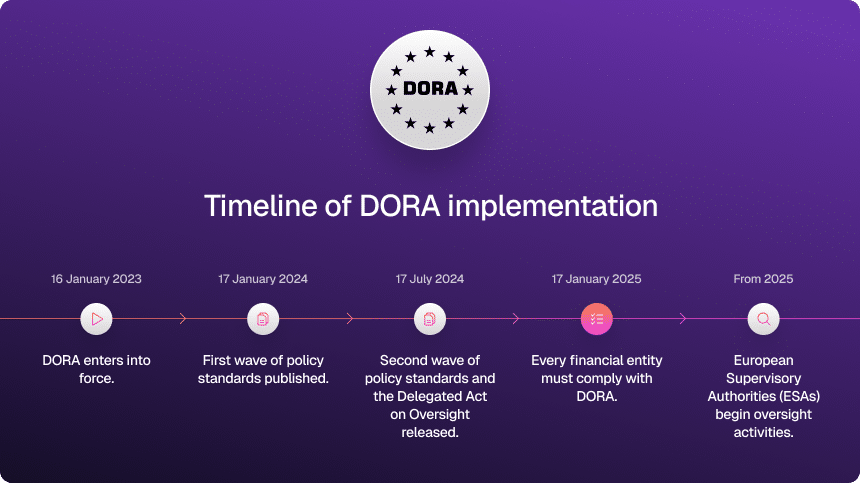
Let’s decode the timeline, because it is more than a series of EU press releases. Each milestone quietly shifted the bar on what “prepared” should look like.
By now, you are not in the “preparation” phase anymore. You are in the “show us what you actually built” phase.
And yes, there is a twist: some delegated and implementing regulations are still being finalized or entering into effect on a rolling basis, which means compliance is not a one-and-done project. It is an ongoing alignment exercise with evolving Level 2 rules and guidance from ESAs and national competent authorities.
If your internal story is still, “We are waiting for the final guidance,” you are out of sync with where supervisors are. They expect a working framework that can adapt as the last pieces of the puzzle drop in.
What You Should Already Have In Place Under DORA
With the DORA deadline behind us, regulators assume you have moved past slideware. They will want to see actual processes, tooling, and evidence.
At a minimum, your organization should be able to show how it meets the core obligations around ICT risk, incidents, testing, third-party risk, and information sharing.
If you can only show spreadsheets and a few static policies, that is a red flag. DORA expects traceability: risks linked to controls, controls linked to tests, tests linked to findings, findings linked to remediation, and all of it living inside a governance loop that reaches your management body.
In other words, your DORA story has to be more than “we wrote a policy.” It has to be “here is how we run this, every quarter, every incident, every vendor onboarding.”
Don’t know if you’re DORA-compliant?
We’ve created a free tool to assess your organization’s DORA readiness in just minutes. Get your compliance score and find gaps now, before auditors do.
Oversight Has Entered The Chat: ESAs, CTPPs, And Real-World Scrutiny
DORA did not stop at telling financial entities to manage ICT risk. It introduced an oversight framework for the big dependencies behind you: cloud providers, core banking vendors, payment processors, and other ICT third-party service providers that are critical to the functioning of the financial system.
From 2025 onwards, the European Supervisory Authorities (ESMA, EBA, and EIOPA) are moving through a clear sequence. National competent authorities submit registers of ICT third-party arrangements by set deadlines, the ESAs perform criticality assessments, and Critical ICT Third-Party Providers (CTPPs) are then designated and brought into an EU-level oversight regime.
What does this mean for you as a financial entity? It means regulators will look at two things at once.
First, whether your own ICT risk management, incident handling, and testing frameworks are live and proportionate.
Second, whether you actually understand and manage your exposure to the providers that keep your services running. If a hyperscaler or core SaaS platform you rely on is designated as critical, the quality of your relationship with them will come under more light, not less.
And yes, the enforcement side is real.
Non-compliance under DORA can lead to administrative sanctions, remedial measures, and reputational damage that hurts a lot more than the legal language suggests. Supervisors will care less about your slide deck and more about your incident metrics, test logs, and vendor performance data.
Made For Financial Institutions
Copla Registry
Spreadsheets make auditors think you don’t know what you’re doing. Prove compliance with the DORA ICT Register 5x faster.
Stay ahead of DORA enforcement with Copla
Copla is built for teams that want DORA compliance without burning out their staff or their budget. By pairing an automation-first platform with expert CISOs, Copla delivers 4 main advantages:
- Helps to reduce compliance workload by up to 80%
- Automates key DORA compliance tasks
- Guides you through the compliance process step-by-step
- Provides CISO-level leadership without the overhead
On top of that, clients typically save over €60K per year compared to hiring in-house staff to handle the same compliance workload, while staying continuously audit-ready.
The only DORA compliance management platform you’ll need
Copla brings together capabilities such as asset and risk registries, evidence mapping, audit verification, regulatory reporting, vulnerability management, awareness training, and incident tracking — all in one place.
FAQ
-
When does DORA come into force? +
DORA entered into force on 16 January 2023, but it applies from 17 January 2025. In plain terms: since 17 January 2025, financial entities and in-scope ICT providers are expected to be DORA-compliant, not “getting ready someday.”
-
What are the key dates I should be aware of? +
Three to pin on your wall: 16 January 2023 (DORA enters into force), 17 January 2025 (DORA starts to apply), and 2025 onward, when EU and national supervisors ramp up oversight, including of critical ICT third-party providers.
-
What does DORA implementation involve? +
Implementation means building a working framework around five pillars: ICT risk management, incident reporting, resilience testing, ICT third-party risk, and information sharing. You are expected to document it, automate where sensible, test it regularly, and produce evidence on demand for auditors and supervisors.
-
What happens if we miss the DORA compliance deadline? +
You do not “miss and move on.” Supervisors can impose remediation measures, enforcement actions, and financial or operational restrictions. More importantly, gaps in DORA readiness usually mirror real resilience weaknesses—so you are taking both regulatory and cyber risk at the same time.