Every few weeks, I hear the same question from UK firms: “Does DORA apply to us?” On the surface, it feels like a Brexit question. The EU passed the Digital Operational Resilience Act (DORA), the UK has its own regime, so surely they’re separate worlds.
They aren’t.
If you operate in or sell into the EU financial sector, DORA is already shaping what “good” resilience looks like for you. And even if you are purely UK-focused, the direction of travel is the same: tighter ICT risk management, tougher testing, and serious expectations around third-party oversight.
In this article, I want to unpack how DORA interacts with the UK’s operational resilience framework, where the overlaps and gaps are, and what practical steps you can take to stay ahead without building two completely separate compliance universes.
Download our free DORA compliance checklist template
Why DORA Still Matters For UK Firms
When the EU introduced DORA, the goal was clear: create a single, consistent digital operational resilience framework for the EU financial sector. It pulls together ICT risk, incident reporting, testing, and third-party oversight into one regulation instead of leaving it scattered across different directives and guidelines.
If the story stopped at “EU regulation,” UK firms could shrug and move on. But DORA comes with extraterritorial reach. If you serve EU financial entities or act as a critical ICT third-party provider to them, DORA follows you home, regardless of where you are legally based.
So even though there is no such thing as “DORA legislation in the UK,” there are plenty of UK organizations that still need to care. If you are embedded in EU financial value chains, your operational resilience posture will be judged against DORA standards, whether your primary regulator is the FCA, PRA, or an EU supervisor.
The bottom line is simple: if EU business or EU clients matter to your strategy, DORA will matter too.
PRO TIP
Map your EU footprint first. Quickly list any business lines or service-providers with EU-based clients. If more than 10% of revenue comes from the EU, build a cross-border compliance checklist—so you’re not caught off guard by DORA’s extraterritorial reach. By the way, Copla does this automatically.
Does DORA Apply To UK Firms? It Depends, But Not Randomly
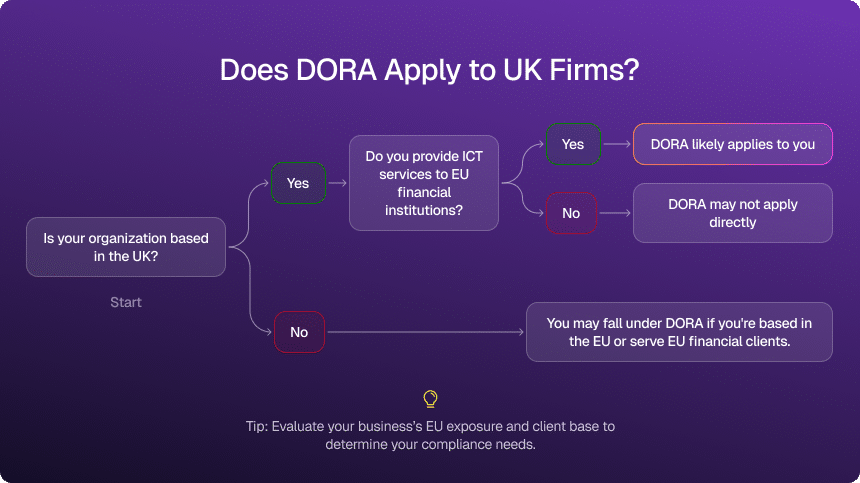
The frustrating answer, “it depends,” is actually quite structured if you break it down. You should seriously consider DORA applicability if any of the following are true:
- You provide financial services directly into the EU (e.g., passporting legacy structures, branches, or subsidiaries).
- You are an ICT or cloud provider that EU financial entities depend on for critical or important functions.
- You sit in a group structure where EU-regulated entities rely on UK operations or infrastructure.
In those cases, DORA does not politely stay on the EU side of the Channel. It shapes group-wide policies, testing expectations, and third-party requirements that will land on your desk in the UK.
At the same time, you already have a strong local regime to deal with. The Bank of England, PRA, and Financial Conduct Authority (FCA) have built their own operational resilience and outsourcing frameworks, with concepts such as “important business services,” “impact tolerances,” and severe-but-plausible scenario testing.
So most cross-border firms are not choosing between DORA and UK rules. They are juggling both—and the smart ones are designing a single resilience strategy that can satisfy both regimes with minimal duplication.
Aligning UK And EU Digital Operational Resilience Strategies
Long before DORA, the UK was already pushing firms toward operational resilience. The FCA and Regulation Authority (PRA) expect you to identify important business services, set impact tolerances, and test your ability to stay within those tolerances under stress.
DORA takes a slightly different angle. Where UK rules start from business services and work backward into ICT, DORA starts from ICT and works outward into the business. UK regulators talk about “important business services.” DORA talks about ICT assets, ICT-supported processes, incident timelines, and digital resilience testing.
Think of it like two camera angles on the same system. One zooms in from the customer-facing service. The other zooms in from the infrastructure that keeps everything running. When you align them, you get a 360° view.
In practice, many firms find that by mapping their UK operational resilience program to DORA’s language, they unlock efficiencies instead of doubling the workload. A single set of risk assessments, testing plans, and incident playbooks can feed both UK and EU requirements, as long as the definitions line up clearly.
PRO TIP
Harmonize your definitions. Create a one-page “glossary” mapping UK terms (e.g., “important business services”) to DORA’s ICT-centric language. This makes it easy for stakeholders to see where existing PRA/FCA processes already satisfy—and where they need to extend for—EU requirements.
Mandatory Cybersecurity Regulations In The UK Versus DORA
UK organizations already sit under a mix of mandatory cybersecurity and resilience obligations. These frameworks are complementary to DORA but differ in scope and level of prescription.
| Regulation / framework | Scope | Key cybersecurity requirements | Comparison with DORA |
| NIS regulations 2018 | Operators of essential services and digital service providers | Implementation of appropriate cybersecurity measures; incident reporting; risk management | Broad, sector-agnostic obligations; less detailed on ICT-specific testing and third-party oversight than DORA |
| FCA and PRA operational resilience guidelines | UK financial institutions including banks, insurers, and investment firms | Robust ICT risk management; incident reporting; business continuity planning; cybersecurity controls | Strong focus on operational resilience and local market context; less prescriptive on a unified ICT framework than DORA |
| Cyber Essentials scheme | Organizations working with government and critical infrastructure | Basic cybersecurity hygiene controls; regular risk assessments | Voluntary and foundational; significantly less comprehensive and detailed than DORA’s resilience regime |
UK regulations set a high bar for outcomes—stay within impact tolerances, protect critical services, manage cyber risk. DORA adds a more detailed, uniform blueprint: how to structure ICT risk frameworks, how to classify incidents, how to test resilience, and how to manage critical third parties.
For firms that operate in both UK and EU markets, this can be turned into an advantage. If you adopt DORA as the “spine” of your ICT resilience framework and map UK regulatory expectations into it, you avoid parallel systems. One testing plan, one incident taxonomy, one third-party oversight model—but able to produce the right evidence for both sets of supervisors.
Unpacking The Technical Standards Of DORA
DORA’s real impact comes through its Regulatory Technical Standards (RTS) and Implementing Technical Standards (ITS). These spell out what your frameworks must actually do. For UK entities with EU exposure, they shape five main areas:
- ICT risk management frameworks.
- Incident reporting and classification.
- Digital operational resilience testing.
- Third-party risk management.
- Information sharing and cooperation.
Building A Robust ICT Risk Management Framework
Under DORA, an ICT risk framework must be structured, continuous, and owned at senior level. It is not enough to say “we manage ICT risk”; you need to show how.
A key element is lifecycle management. Every critical system should be tracked from procurement to decommissioning, with patching, configuration, and dependencies monitored throughout. Untracked legacy systems are exactly the kind of blind spot DORA aims to eliminate.
Standardizing Incident Reporting And Classification
DORA expects clear, consistent incident handling. Firms must define thresholds for what counts as a major ICT-related incident, classify incidents accordingly, and report major ones within set timelines.
That means incident taxonomies, predefined severity levels, escalation paths, and templates for regulator reporting. Post-incident analysis is not optional: you are expected to capture lessons learned and feed them back into your risk framework so the same failure does not keep repeating.
Strengthening Digital Operational Resilience Testing
A single annual penetration test does not meet DORA’s idea of resilience testing.
DORA requires a risk-based program that can include vulnerability assessments, advanced security testing, scenario-based exercises, and for some entities, threat-led penetration testing (TLPT). The goal is to simulate realistic attacks and disruption, then fix what you find.
UK firms already involved in CBEST or TIBER-UK have a strong head start. The next step is aligning scope, documentation, and follow-up with DORA’s expectations so one testing program satisfies both regimes.
Enhancing Third-Party Risk Management
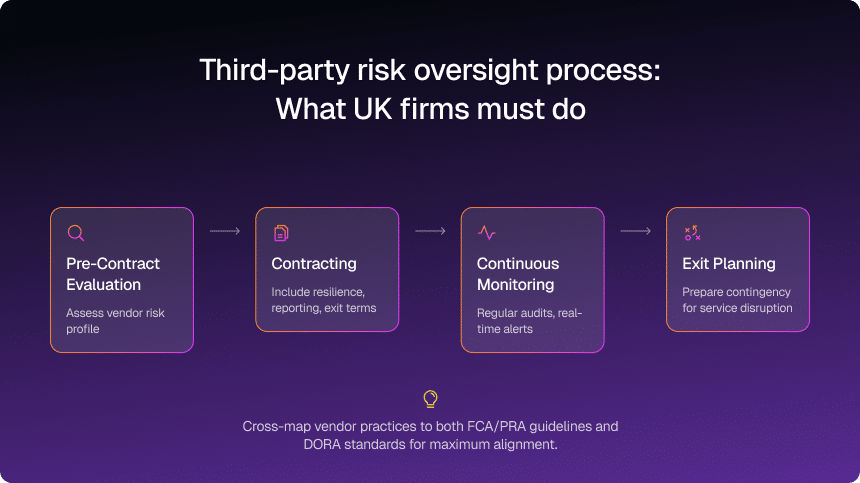
DORA is very direct about third-party risk: if your resilience depends on someone else’s system, regulators expect structured oversight.
This includes pre-contract due diligence, robust resilience and security clauses, audit and access rights, ongoing monitoring, and credible exit plans for critical or important services. That approach lines up well with UK outsourcing and third-party rules; the gap is often in execution, not concept.
Ensuring Information Sharing And Cooperation
Finally, DORA pushes firms toward structured information sharing. Cyber threats move too fast for each institution to operate in a vacuum.
Participation in sector information-sharing schemes, cross-border crisis coordination, and joint exercises all contribute to what supervisors view as “good” resilience practice. For cross-border groups, the challenge is to connect UK and EU processes so information does not get stuck on one side.
PRO TIP
Build an “ICT asset lifecycle” registry. List each critical system from procurement to decommission. Tag them with owner, version, and retirement date — so when you hit DORA’s lifecycle mandate, you can prove every patch, update, or sunset plan in minutes. Copla does this automatically.
Practical steps for UK entities
Even though DORA is not UK law, its standards are fast becoming a reference for financial sector resilience globally. Many UK firms are aligning voluntarily to keep EU market access and avoid being the weak link in a group or value chain.
Adopting International Standards For Cybersecurity And Business Continuity
International standards are a practical way to align DORA, UK rules, and internal governance. Two are especially relevant: ISO/IEC 27001 and ISO 22301.
| Standard | Purpose | Key benefits |
| ISO/IEC 27001 | Establishes a structured Information Security Management System (ISMS) to protect digital assets. | Strengthens cybersecurity, supports regulatory alignment, and reduces likelihood and impact of ICT incidents |
| ISO 22301 | Focuses on Business Continuity Management (BCMS) to maintain operations during disruptions. | Enhances crisis response, minimizes downtime, and aligns with resilience and continuity testing expectations |
Mapped correctly, these standards cover a large portion of what DORA and UK regulators expect around policies, risk, controls, and improvement. You are tuning the system, not building from scratch.
Strengthening third-party risk management practices
Third-party risk is rising fast on both UK and EU agendas. A simple, structured model goes a long way.
| Third-party risk management practice | Implementation strategy |
| Pre-contract risk assessments | Evaluate vendor security protocols and resilience measures before engagement. |
| Robust contractual agreements | Include resilience clauses specifying security expectations, uptime guarantees, and incident reporting obligations. |
| Ongoing monitoring and audits | Continuously track vendor performance, conduct security audits, and assess compliance with resilience standards. |
| Exit strategies and contingency planning | Develop a transition plan in case of vendor failure, ensuring minimal business disruption. |
Design this once with both UK and DORA in mind and you will avoid maintaining two incompatible vendor oversight systems.
Don’t know if you’re DORA-compliant?
We’ve created a free tool to assess your organization’s DORA readiness in just minutes. Get your compliance score and find gaps now, before auditors do.
Improving incident response and resilience testing
Good incident response is now a baseline expectation, not a “nice to have.”
| Incident response measure | Implementation approach |
| Predefined classification thresholds | Establish clear criteria for classifying and escalating major ICT incidents. |
| Incident playbooks | Develop response strategies for different cyber threats, including ransomware and data breaches. |
| Real-time threat monitoring | Deploy automated detection tools for faster response and mitigation. |
| Post-incident analysis | Conduct root cause analysis to improve future resilience. |
Beyond incident response, firms must also implement rigorous resilience testing to identify vulnerabilities before attackers do.
| Resilience Testing Method | Purpose |
| Threat-led penetration testing (TLPT) | Simulates cyberattacks to uncover vulnerabilities before they are exploited. |
| Scenario-based stress testing | Evaluates system response under extreme operational pressures. |
| Tabletop exercises | Trains executives and IT teams on real-world cyber crisis scenarios. |
If you already do CBEST or TIBER-UK, you are close to the DORA mindset. Extending those practices across more systems and documenting them against DORA’s requirements is usually the most efficient path.
Why Copla Is the Smart Way to Ensure DORA Compliance in the UK
Copla is built for teams that want DORA compliance without burning out their staff or their budget. By pairing an automation-first platform with expert CISOs, Copla delivers 4 main advantages:
- Helps to reduce compliance workload by up to 80%
- Automates key DORA and NIS2 compliance tasks
- Guides you through the compliance process step-by-step
- Provides CISO-level leadership without the overhead
On top of that, clients typically save over €60K per year compared to hiring in-house staff to handle the same compliance workload, while staying continuously audit-ready.
The only compliance management platform you’ll need
Copla brings together capabilities such as asset and risk registries, evidence mapping, audit verification, regulatory reporting, vulnerability management, awareness training, and incident tracking — all in one place.
FAQ
-
Does DORA apply to UK-based companies? +
Not automatically. DORA is an EU regulation, but it still hits UK firms that serve EU financial entities or act as critical ICT providers to them. If you are in their supply chain, DORA is your problem too.
-
What types of UK firms need to consider DORA compliance? +
Any UK financial institution serving EU clients, UK branches or subsidiaries of EU firms, and ICT/ cloud/fintech providers supporting critical or important functions for EU financial entities. If EU supervisors or EU clients rely on you, DORA should be on your radar.
-
Should UK firms implement DORA even if they are not legally required? +
In many cases, yes. Aligning with DORA gives you a modern, structured resilience framework and keeps you compatible with EU partners, groups, and investors. Treat it as a strategic upgrade, not just a legal burden.